Here are the five little things that make us special!
The Problems Our Customers Face:
- Poor digital strategy, poor cyber strategy, poor cybersecurity tools and processes, dangerous silos, poor cyber training, nebulous reorgs, too much risk, needless rework, compliance violations, redundant complexity, poor culture of technology and learning, ineffective bureaucracy, contradicting assessment findings, failure to understand the critical path, poor leadership, prior data breaches or incidents, and/or poor or ambiguous communication – all the while security and IT performance gaps worsen or stay flat with you footing the bill. There is a better way – the Abstract Forward way!
The Solutions We Provide:
- Savvier than top-tier consulting firms without the excessive cost, more creative than top jazz artists, more premier than European automotive engineering, and an amazing ROI. A truly premier digital strategy and security management consulting firm. We bring together three consulting firms types for a disruptive solution: IT Nerd/Hacker, Creative Agency, and Risk Assurance. We are not afraid to be different and challenge status quo conceptions in business technology, because we prove the ROI, but don’t take our word for it see our A+ results and then contact us with your biggest challenge.
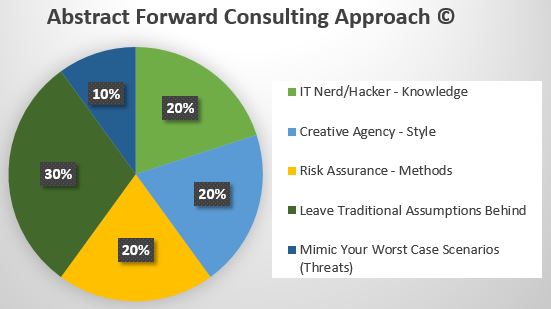 Leaving traditional assumptions behind is key at 30% because it has historically held organizations back. Disrupting what has been reduces organizational bias, opens siloed communication, and reduces needless office bureaucracy thereby reducing risk. It also means we are not limited by traditional frameworks, templates, or consulting approaches. In security, it’s about the now and understanding the threat actors approach.
Leaving traditional assumptions behind is key at 30% because it has historically held organizations back. Disrupting what has been reduces organizational bias, opens siloed communication, and reduces needless office bureaucracy thereby reducing risk. It also means we are not limited by traditional frameworks, templates, or consulting approaches. In security, it’s about the now and understanding the threat actors approach.
Most organizations would admit that their security and business processes could be improved. Knowing where and how is the challenge we excel at. We do it in a disruptive way that requires organizations ready to improve. We do different, not to be different, but to be better amid the democratization of technology. We confront worst case scenarios so you are trained, defended, not surprised, and most importantly to maintain your customers with a competitive edge. Like the military, we must be realists to plan for the optimal outcome amid many risks. Mimicking your worst-case scenarios is key to putting policies, procedures, and the right people in place to reduce vulnerabilities. As most companies evolve over time, they become more dependent on technology while most vulnerabilities are tied to the internet. This is one of the reasons why we have a board definition of vulnerability: “Any weakness that can be exploited by an aggressor to make an asset susceptible to hazard or damage”.
- Risk = threat * vulnerability * consequences.
- This can be an 18-year-old hacker from Eastern Europe, an underpaid or demoted employee, a cryptic botnet, or anything else with means and intent.
- We make no assumptions without solid evidence and reasoning supporting it – this is not checkbox compliance.
- We can and will obtain good intelligence for our clients.
| The following process diagram outlines the relationships that need to be understood for good risk management. This diagram could be successfully applied to most of our corporate clients. 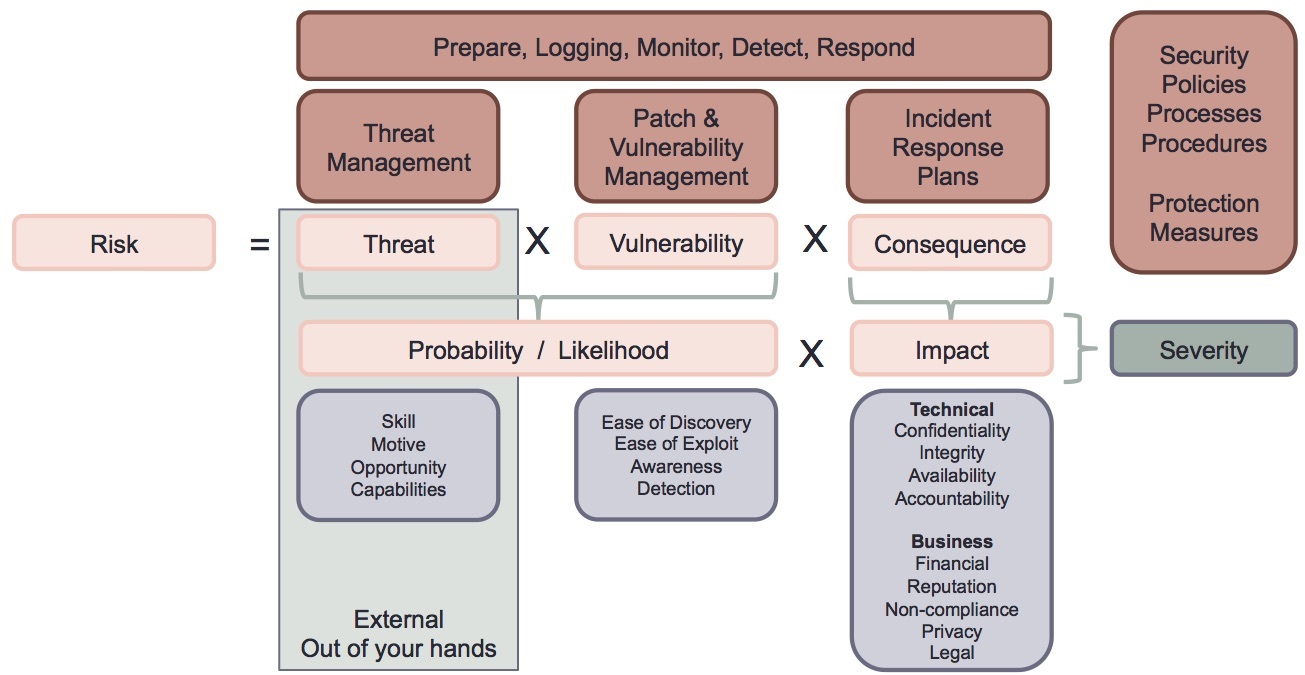
| This diagram shows the cross-functional relationships and sub-dependencies among critical infrastructure sectors. We are DHS ICS CERT trained to help you navigate these complexities. 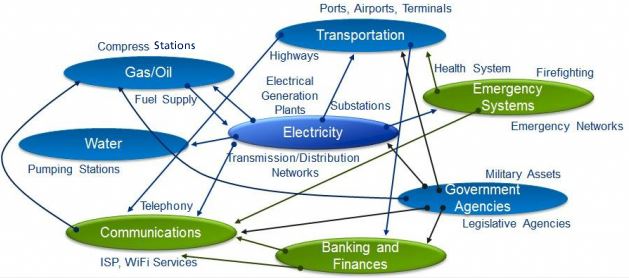
|


 Leaving traditional assumptions behind is key at 30% because it has historically held organizations back. Disrupting what has been reduces organizational bias, opens siloed communication, and reduces needless office bureaucracy thereby reducing risk. It also means we are not limited by traditional frameworks, templates, or consulting approaches. In security, it’s about the now and understanding the threat actors approach.
Leaving traditional assumptions behind is key at 30% because it has historically held organizations back. Disrupting what has been reduces organizational bias, opens siloed communication, and reduces needless office bureaucracy thereby reducing risk. It also means we are not limited by traditional frameworks, templates, or consulting approaches. In security, it’s about the now and understanding the threat actors approach.
















 Mr. Swenson is open to
Mr. Swenson is open to  independently write, co-author, commentate on radio or T.V., or be a source for journalists. He is also open to speak at companies, universities, non-profits, think tanks, and at private events on a selective basis. He can be a moderator, speaker, or panel member. If you are looking for a non-big-four opinion from someone with an exceptionally amazing background, with varied roles and responsibilities in business and a track record of authentic leadership and innovative thinking and writing, he offers the best m
independently write, co-author, commentate on radio or T.V., or be a source for journalists. He is also open to speak at companies, universities, non-profits, think tanks, and at private events on a selective basis. He can be a moderator, speaker, or panel member. If you are looking for a non-big-four opinion from someone with an exceptionally amazing background, with varied roles and responsibilities in business and a track record of authentic leadership and innovative thinking and writing, he offers the best m