Most organizations view IT as a cost center that generates business data which is increasingly used to make business decisions. As a result, these assets need to be vigorously protected from both internal and external threats. Cyber liability insurance is an undeniable but imperfect way to protect these assets.

1. Cyber Liability Insurance Defined:
Cyber liability or data breach liability insurance is designed to reduce the risk of civil litigation and other penalties after a hack or data breach
Business interruption is the most common type of loss from a cyber indecent. You want data breach coverage in place because fast action is required to help restore the public’s confidence if your business is victimized by a hack or data breach. Note that each carrier and industry will define it uniquely.
2. Executives and Managers Have a Heightened Duty to Protect Systems and Data – No Exceptions:
Boardrooms are concerned with comprehensive information security, data protection, brand reputation, broad management liability
It is essential that IT teams
One of the risk transfer decisions is how much cyber insurance to have, then selecting the correct endorsements and exclusions based on the industry, other insurance coverages, prior events, and the like.
Observing this complexity, IT and business executives need to understand cyber insurance and what role they play in defining cyber coverage. IT involvement is a critical aspect of the organization’s overall cyber risk management strategy for digital and even physical assets.
3. Your Assets, Risks, and Needed Coverages Must be Detailed and Ongoing:
What are your company’s greatest assets – including in hidden areas?
Have you had any bad events, business or technology related?
Were they documented and reported? They could impact current coverage and future coverage.
What concerns keep you up at night, or consume more than their share of your attention in the day?
What are your key processes? Do you have any procedures that are not tied to computers?
What is the 15% of your business that is not central to the operation, but is crucial because it distinguishes your company from others and opens the door for more clients to new markets?
Are your backup systems in place and ready to be activated at a moment’s notice?
Do your insurance coverages, business or technology related, match your risks and cover your assets?
4. General Liability Coverage Won’t Cover Data Breaches and Hacks:
Cyber insurance is almost always excluded from general liability policies unless you pay extra for and specifically define your cyber coverage needs.
Keep in mind most general business liability insurance policies and terms were drafted before hacking was invented so they are by default behind the technology. Most often general liability business insurance covers bodily injuries and property damage resulting from your products, services or operations.
Many business owners overstate the risk of a workplace slip and fall injury and fail to adequately quantify cyber risk at all because it is a newer digital risk and you can’t see or touch it.
5. Cyber Liability Insurance Typically Covers Both First-Party and Third-Party Losses:
First-party losses include the breach response costs a company would incur to notify and communicate with the people impacted by a breach, conducting forensic analysis, hiring legal counsel and a crisis management team.
First-party cyber coverage may also pay for the loss or restoration of digital or network assets, trade secrets, intellectual property
First-party coverages are often subject to a deductible.
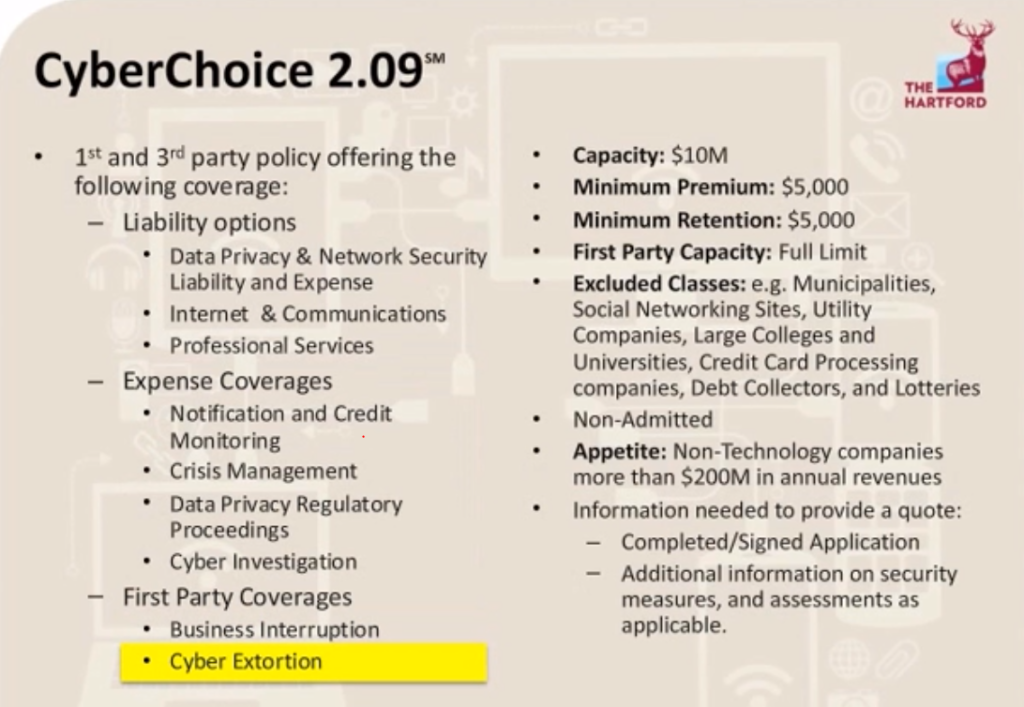
Hartford, 2019.
Cyber extortion (ransomware) is another first-party coverage that pays the costs to terminate incidents in which criminals hold (or threaten to hold) a company’s network hostage in exchange for a ransom.
Many policies cover income you lose and extra expenses you incur to avoid or minimize a shutdown of your business after your computer system fails due to a covered peril. The perils covered may be the same as those excluded under the common Damage to Electronic Data exclusion for general liability. The loss of income and extra expense coverages afforded under a cyber liability policy differ from those provided under your commercial property policy.
Network security liability insurance covers lawsuits against you due to a data breach or to the inability of others to access data on your computer system. Coverage may apply if the data breach or inability to access your system is due to a denial of service attack, a virus, malware or unauthorized access and use of your system by a hacker or rogue employee. Policies may cover lawsuits alleging that you failed to adequately protect data belonging to customers, clients, employees or other parties.
Network privacy liability insurance covers lawsuits based on allegations that you failed to properly protect sensitive data stored on your computer system. The data may belong to customers, clients and other parties. Some policies cover liability arising from the release of private data (such as social security numbers) belonging to your employees.
Electronic media liability insurance covers lawsuits against you for acts like libel, slander, defamation, copyright infringement, invasion of privacy or domain name infringement.
6. Providing Timely Notice of Claim Is Key:
Claims-made coverage responds when a “claim,” as defined in the policy, is first made against an insured, irrespective of when the underlying incident occurred. Discovery-triggered coverage responds when the insured develops a reasonable belief that a first-party loss potentially covered by the policy may have occurred, even if the nature and extent of the loss are unknown (Jeanne Deni and Andrew Moss, 2019).
Notice is generally required as soon as practicable after a claim is made or loss discovered, and policies may require that notice be received during the policy period. In addition to timely notice, some cyber policies (most in our experience) may require a sworn proof of loss statement within 90 to 180 days after discovery of certain first-party losses.

It is thus critical that company personnel in a position to detect potentially covered claims or losses have a working understanding of the scope of coverage and how it is triggered so that information is promptly communicated to management responsible for notifying the company’s insurance carriers. N
7. Pre-Select Breach/Hack Counsel and Vendors:
Normally cyber insurance policies require underwriter approval of the use of breach/hack vendors. (FSSCC, Cyber Insurance Buying Guide, 2016).
Pre-selection is critical because the last thing an organization should be worried about is whether their insurance provider will approve their selected breach counsel and forensics firm. It also helps you document your incident response plan (Financial Services Sector Coordinating Council, Cyber Insurance Buying Guide, 2016).

8. Prepare for Likely Coverage Exclusions/Sub-limits:
Portable Electronic Device Exclusion
a) If the device leading to a cyber breach is portable, many policies could exclude coverage completely for any resulting loss (Financial Services Sector Coordinating Council, Cyber Insurance Buying Guide, 2016).
Intentional Acts Exclusion
a) What is intentional and by whom is highly confusing, and what about mere negligence viewed as intentional – easy denial case for the carrier.
b) A crime or fidelity policy generally covers first-party loss to the Insured even where such loss is caused by the Insured, while liability policies generally provide for damages or losses the Insured causes to a third party (Financial Services Sector Coordinating Council, Cyber Insurance Buying Guide, 2016). Most cyber insurance policies do not adequately provide for both first-party and third-party loss. For example, liability policies typically exclude coverage for damages or losses intentionally caused by an Insured. Thus, if an employee accidentally caused a cyber breach, the resulting loss would be covered (either under a general liability or umbrella policy that does not exclude cyber perils or under a stand-alone cyber policy). However, if a different employee caused the exact same cyber breach intentionally, the resulting loss would be denied under a general liability policy if this exclusion is present (Financial Services Sector Coordinating Council, Cyber Insurance Buying Guide, 2016).
Nation/State, Terrorism, Cyber Terrorism Exclusions/Acts of God
Acts of God exclusions can result in coverage being precluded simply based on who or what caused the breach to occur. For example, if a terrorist attack resulted in an explosion at an organization’s facility or a tornado caused massive damage to an organization’s power source, the resulting losses may not be covered under a standard cyber policy. Fundamentally, companies expect cyber insurance to cover their losses whenever a cyber breach happens, regardless of who caused it or why
Negligent Computer Security Exclusion
Some policies exclude coverage if data is unencrypted or if the Insured has failed to appropriately install software updates or security patches.
Data on Unencrypted Devices or BYOD
Some policies do not cover devices that are unencrypted or non-company-owned devices.
Territorial Limits
Some coverage is limited only to incidents that occur in the United States and an organization may need additional coverage depending on where data is stored.
Sub-Limits
Many policies also have sub-limits that may apply for things like breach notification costs, forensic expenses, credit monitoring costs, business or Post-Breach Services. Some insurers are starting to partner with cybersecurity specialists to assist customers who experience a cyber breach with forensic investigations, proactive incident response strategies, and training as they realize the benefit both to the customer and themselves in responding as quickly and efficiently as possible to a cyber breach to keep resulting costs, claims, and damages as low as possible.
9. Insurance Companies Tend to Deny Cyber Liability Issuance or Claims Coverage When One or More of These Items Are Present:
a) Inadequate cybersecurity testing procedures and audits. They should be independent and auditable.
b) Inefficient processes to stay current on new releases and patches
c) Inadequate cyber incident response plans. They must be detailed, written, up to date, and must be practiced.
d) Inadequate backup processes and recovery procedures. This assumes you have a data classification scheme and network segmentation, and that you have tested the speed of your back up.
e) Inadequate policies concerning the security of vendors and business partners. How you measured their risk and criticality to your business. Then put mitigating controls in place or cut the vendor.
f) Poor-quality security software and employee training. Training on phishing, social engineering, and acceptable use of company data and technology.
g) Lack of adherence to a published security standard. Your policies and procedures should generally conform to the standard that most closely fits your industry and company: Cobit 5, NIST CSF, ISO 27001, etc.
10. Evaluating Cyber Liability Carriers:
The way to compare carriers is via their A.M. best rating, time in business, market share, S&P credit rating, industries excluded from coverage, premium cost, and amount of premium written.
You can also ask a broker for their assessment since they get feedback from many clients, etc.
Also, consider the country of legal jurisdiction.
Here are two carrier examples:
Chubb Insurance of Switzerland (Cynthia Harvey,
The world’s largest publicly traded property and casualty insurance company and the largest commercial insurance provider in the United States.
a) The company launched its first “cyber risk” product in 1998.
b) Direct premiums written: $316.3 million.
c) Market share: 17.0 percent
d) S&P rating: AA
e) A.M. Best rating: A++ (Superior)
f) Most risk classes eligible for at least $10 million in limits; maximum capacity of $100 million available through Chubb’s Global Cyber Facility.
Chubb Cyber Insurance Product Descriptions:
a) Enterprise Risk Management (ERM) product is for large organizations in a wide array of industries.
b) DigiTech ERM offers enhanced protection tailored to the needs of technology companies, consultants and systems integrators, data processors and software developers. Integrity+ offers separate policies for claims made by customers, vendors, suppliers
c) ForeFront Portfolio 3.0 is tailored for private companies and includes crime insurance, kidnap ransom and extortion insurance, workplace violence expense insurance, and several other kinds of insurance, in addition to cyber insurance.
Beazley Insurance of London (Cynthia Harvey, eSecurity Planet.com, 11/09/18)
This insurance company offers marine, political, accident and contingency, property, reinsurance (insurance for insurers) and specialty products, which includes its cyber insurance business.
Founded in 1986, it is headquartered in London and does business in the U.S. Europe, Canada, Latin America and Asia. In 2018, it won multiple awards including Launch of the Year for Beazley Smart Tracker, Risk Carrier of the Year, Innovative Initiative for Weather Guard, Insurance CEO of the Year and Insurer of the Year.
a) Direct premiums written: $95.0 million
b) Market share: 5.1 percent
c) S&P rating: A+ (Strong)
d) A.M. Best rating: A (Excellent)
e) Limits: Up to $15 million with BBR, but additional coverage is available through BBR Boost.
f) Beazley has been providing cyber insurance since 2009.
Beazley Cyber Insurance Product Description:
a) Beazley calls its cyber insurance Beazley Breach Response (BBR). The company claims that it offers 360-degree protection against all cyber risks.
b) This includes BBR Services, a business unit dedicated to helping organizations manage their response to incidents. It includes forensics experts, specialized lawyers and public relations professionals who can help organizations address breaches. Through a partnership with Lodestone Security, it also offers pre-breach services.
Lastly, we will be doing a cyber liability podcast to talk through these items in detail soon. See our podcast here.
By Greg Coon, Tim Olish, and Jeremy Swenson (Lead Writer & Editor).
© Abstract Forward Consulting, LLC. 2019. All rights reserved. Contact us here.
Disclaimer: This article does not represent the views of former or current employers and / or clients. Non-public information will not be disclosed. Information obtained in this article may be materially out of date at or after the time of the publication. This article is not legal, accounting, audit, health, technical, or financial advice.
