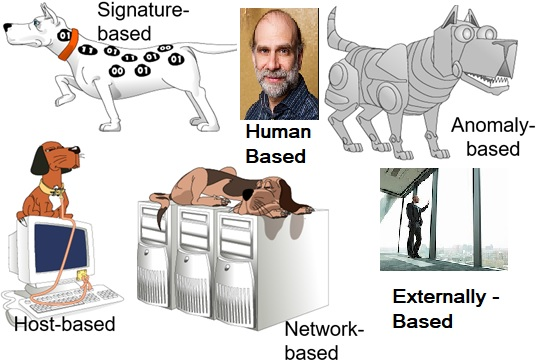
The best way to detect precursors to data exfiltration is to employ a six-prong detection approach applied to all risk areas as practicable. Figure 1. shows the six-pronged detection approach.
Figure 1. Six-Pronged Data Exfiltration Precursor Detection Approach [1] [2].
1) Signature Based.
Characteristics: 1) Uses known pattern matching to signify attack; 2) Former zero days, known exploits, etc.
Advantages: 1) Widely available; 2) Most antivirus is based heavily on this; 3) Fairly fast; 4) Easy to implement; 5) Easy to update.
Disadvantages: 1) Cannot detect attacks for which it has no signature – Zero days; 2) Insider threat.
2) Host Based.
Characteristics: 1) Runs on a single host; 2) Can analyze audit-trails, logs, the integrity of files and directories, etc.
Advantages: 1) More accurate than NIDS; 2) Less volume of traffic so less overhead.
Disadvantages: 1) Deployment is expensive; 2) No plan for if the host gets compromised – Real risk for organizations with more than 10 thousand employees.
3) Human Based [2].
Characteristics: 1) Has the unique experience set deriving intuition; 2) Has five senses.
Advantages: 1) Has the ability to learn multiple tools and connect the dots; 2) Can set team direction and inspire people; 3) Can think creatively; 4) Can think with the voice of the customer or recipient of a phishing e-mail.
Disadvantages: 1) Bias and ego; 2) Cannot calculate large numbers fast.
4) Anomaly Based.
Characteristics: 1) Uses statistical model or machine learning engine to characterize normal usage behaviors; 2) Requires big data and other software tools; 3) Recognizes departures from normal as potential intrusions.
Advantages: 1) Can detect attempts to exploit new and unforeseen vulnerabilities; 2) Can recognize authorized usage that falls outside the normal pattern.
Disadvantages: 1) Generally slower, more resource intensive compared to signature-based tools; 2) Greater complexity, difficult to configure; 3) Higher percentages of false alerts.
5) Network Based.
Characteristics: 1) NIDS (network intrusion detection system) examine raw packets in the network passively and triggers alerts.
Advantages 1) Easy deployment; 2) Unobtrusive; 3) Difficult to evade if done at the low level of network operation.
Disadvantages: 1) Fail Open; 2) Different hosts process packets differently; 3) NIDS needs to create traffic seen at the end host; 4) Need to have the complete network topology and complete host behavior; 5) Highly unlikely.
6) Externally Based.
Characteristics: 1) Studies show there are 258 externally measurable characteristics about network infrastructure (without any inside info).
Advantages: 1) Beaching marking – identifying mismanagement symptoms such as poorly configured DNS or BGN networks; 2) Beaching marking – identifying malicious activity which mostly includes SPAM, phishing, and port scanning; 3) One study found it to be highly reliable in predicting breaches (90% true positives in a closed limited test) [3].
Disadvantages: 1) Its low hanging fruit – easy weaknesses to spot; 2) Good I.T. audits and red teaming is similar.
[1] Dash, Debabrata. “Introduction to Network Security”. PowerPoint presentation. 2017. [2] Photo of public figure Bruce Schneier by Per Ervland. https://www.schneier.com/ 2018. [3] Liu, Yang; Sarabi, Armin; Zhang, Jing; Naghizadeh, Parinaz; Karir, Manish; Bailey, Michael; and Liu, Mingyan. “Cloudy with a Chance of Breach: Forecasting Cyber Security Incidents” 2015. Pg. 1.