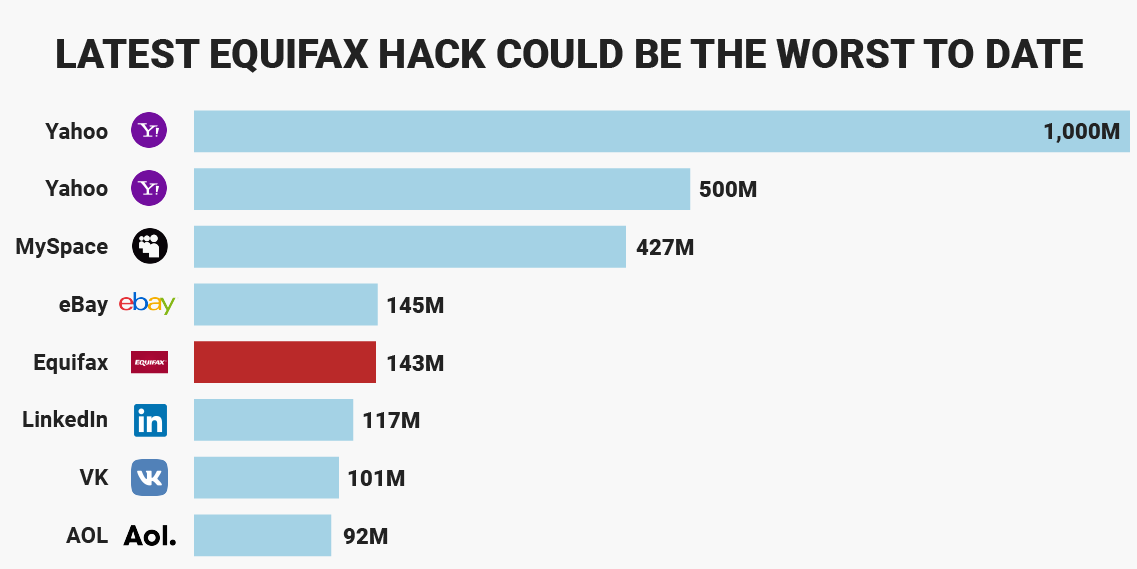
 Minneapolis, MN – 11/22/17. The recent Equifax data breach impacted one-third of the U.S. population with more than 143.5 million records exposed. This epic hack started on 05/13/2017 and lasted until 07/29/2017, all the while the company was clueless. As a result, the threat actors trolled around Equifax’s network, staging and exfiltrating data undetected for 2.5 months. It is one of the biggest data breaches in U.S. history but clearly not the biggest. Going forward, breaches are likely to be bigger, given the threat actors risk vs. reward tradeoff, and the increasing capabilities of cloud computing and botnets thereby enabling anonymity.
Minneapolis, MN – 11/22/17. The recent Equifax data breach impacted one-third of the U.S. population with more than 143.5 million records exposed. This epic hack started on 05/13/2017 and lasted until 07/29/2017, all the while the company was clueless. As a result, the threat actors trolled around Equifax’s network, staging and exfiltrating data undetected for 2.5 months. It is one of the biggest data breaches in U.S. history but clearly not the biggest. Going forward, breaches are likely to be bigger, given the threat actors risk vs. reward tradeoff, and the increasing capabilities of cloud computing and botnets thereby enabling anonymity.
 Yet this breach may be one of the most negatively impactful because of the comprehensive sensitive data lost in it including social security numbers, full names, addresses, birth dates, and even drivers licenses and credit card numbers for some. “This information is the kind that several businesses like financial companies, insurance companies, and other security-sensitive businesses use to identify a customer accessing their accounts from online, by phone, or even in person” (Pelisson, Anaele; & Villas-Boas, Antonio, 09/08/17).
Yet this breach may be one of the most negatively impactful because of the comprehensive sensitive data lost in it including social security numbers, full names, addresses, birth dates, and even drivers licenses and credit card numbers for some. “This information is the kind that several businesses like financial companies, insurance companies, and other security-sensitive businesses use to identify a customer accessing their accounts from online, by phone, or even in person” (Pelisson, Anaele; & Villas-Boas, Antonio, 09/08/17).
Therefore, this breach lends itself perfectly to future identity theft. To date, hundreds of fraudulent loan applications, credit card charges, student loans, and insurance claims have been documented and it’s not likely to stop anytime soon. All of this has inspired negligence lawsuits and regulatory reviews across most states. If there is one thing you would expect from a credit monitoring company claiming to protect the accuracy of your data, it is that they would at least have above average information security standards. Yet they clearly did not. Below are the things that went wrong at Equifax to enable and exacerbate the breach:
1) Equifax’s first problem was that they failed to take a recent critical update notice seriously:
NIST (The National Institute of Standards in Technology) via CERT (critical emergency readiness team) issued an update alert for the Apache Struts platform on 03/08/17, CVE (critical vulnerability exploit) 5638 (Fig 2) which Equifax ignored or gave low priority. Apache Struts is a free, open-source, MVC (model view controller) framework for creating nice, new Java web applications. At Equifax, the Apache Struts platform was used for multiple applications and thus the risk associated with failing to patch the vulnerably was exponentially large and complex.
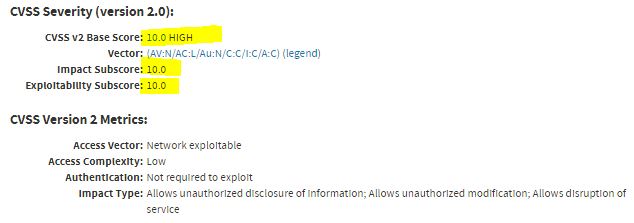
Negatively, the Apache Struts vulnerability allowed remote code execution via a cmd string upload in the HTTP header. Both versions of this vulnerability were listed as being highly severe by the CVE alert. There is no way Equifax did not know this to a considerable degree. Lesson learned: solidify your security baseline and update and patch based on likely impact and ease of execution.
2) Equifax had a history of poor security culture back to 2014 and failed to make key improvements:
“In April 2017, cyber-risk analysis firm Cyence rated the probability of a security breach at Equifax at 50 percent in the next 12 months. Credit analytics firm FICO gave Equifax low marks on data protection — an enterprise security score around 550 on a scale of 300 to 850. In 2014, Equifax “left private encryption keys on its server,” potentially allowing hackers to decrypt sensitive data, according to a recent breach related lawsuit.” (Harney, Kenneth; 11/21/2017). Thus, Equifax had poor security long before the recent breach and they have been warned.
a) Creating a culture of security where rank and title do not suppress valid evidence and reason, and outside vendors are vetted and listened to in a timely order concerning security risks would improve their security posture. Yet this requires cross-departmental collaboration, openness, and it requires firing those insulating themselves in fiefdoms of “yes sayers”.
3) Executives had more concern for short-term profit than long-term security:
On 08/01/17 and 08/02/17 three top executives from Equifax sold nearly $2 million worth of company stock at a high price but maintain that they had no knowledge of the breach that was discovered by the company on 07/29/17. Allegedly these trades were placed before August 2017. Although these may be innocent well-earned stock trades, the totality of the circumstances warrants further validation even though Equifax’s attorneys reviewed the trades at the time. Trades like these should not just be reviewed by the legal department but also by the P.R. department when a disaster is near, likely, or present. Most importantly, long-term security should be on the mind of executives, not short-term profits – implicates a huge culture issue.
4) They have business products that create conflicts of interest that incent data breaches and identity theft:
This is because Equifax sells credit monitoring services at about $17 per month per customer. They also partner to sell identity theft monitoring via LifeLock. LifeLock has a direct copy of most of Equifax’s data so they can accurately monitor for fraud indicators. LifeLock cost about $30 per month per customer and a part of that profit is shared with Equifax via a prearranged deal inked in 2015. Sen. Elizabeth Warren described it in the video below.
5) Equifax used stunningly simple PIN numbers that were composed of date
and time:
This was corroborated by Wes Moehlenbruck, MS, CISSP, CEH, CHFI, a California-based senior cybersecurity engineer with a master of science degree in cybersecurity. He stated, “The PINs used to lock and unlock credit files were simply based on the time and date – nothing more complicated than that. Absolutely yes, this is a rookie mistake” (Hembree, Diana, 11/15/17). Obviously, in using such a simplistic approach in PIN generation, a user’s PIN could easily be guessed or brute-forced by testing every possible combination using a computer program. PINs should be more complex, completely confidential, and there should be a policy mandating that they change often (every six months for example).
If you want to talk more about these and related concepts applied to my consulting and speaking, please contact me here.
