By Mamady Konneh, MSST, and Jeremy Swenson, MBA, MSST.
Minneapolis, MN — Every year we like to review and commentate on the most impactful security technology and business happenings from the prior year. Those likely to significantly impact the coming year in unique ways. Although incomplete, these are six trends worth addressing in order of importance.
Fig 1. (Cyber Trend Mashup Overlay, + Stock Image, 2019).

1) The Media Disinformation War Continues Embracing Artificial Intelligence:
With the advancement of communications technologies, the growth of large social media networks, and with the “appification” of everything— users have morphed beyond merely consuming information to being distributors and sometimes contributors. This ripens the ease and capability of disinformation.
Disinformation is defined as incorrect information intended to mislead or disrupt, especially propaganda issued by a government organization to a rival power or the media. For example, governments creating digital hate mobs to smear key activists or journalists, suppress dissent, undermine political opponents, spread lies and control public opinion (Shelly Banjo, Bloomberg, 05/23/2019). Today’s disinformation war is largely digital via platforms like Facebook, Twitter, iTunes, WhatsApp, Yelp, and Instagram (Fig. 2). Yet even state-sponsored and private news organizations are increasingly the weapon of choice — creating a false sense of validity. Undeniably, the battlefield is wherever a large number of followers are.
We all know that false news spreads faster than real news most of the time, largely because its sensationalized. Since disinformation draws in viewers, which drives clicks and ad revenues,it’s a money-making machine. If you can control what’s trending in the news and/or social media, it impacts how many people will believe it, which in turn impacts how many people will act on that belief, good or bad. This is exacerbated when combined with human bias or irrational emotion.
Bots and botnets are often behind the spread of disinformation, complicating efforts to trace its source and to stop it. Further complicating this phenomenon is the amount of app (application) to app permissions. For example, the CNN and Twitter app having permission to post to Facebook and then Facebook having permission to post to WordPress and then WordPress posting on Reddit, or any combination like this. Not only does this make it hard to identify the chain of custody and source, but it also weakens privacy and security due to the many authentication permissions.
Fig 2. News, Social Media, and Puppet Master of Disinformation (Right, Chandrajit Banerjee, Left Marc Creighton, 2019).

Disinformation campaigns attempted to influence U.S. elections in 2016 — presidential, and 2018 — congressional (Fig. 2). The effects are not fully known to this day yet there is some undeniable impact, with debates on both sides. This taken in conjunction with outdated electoral policies and poor public-to-private partnerships support the conclusion that disinformation capabilities are on the rise leading up to the U.S. presidential election in 2020. In fact, according to one report, the number of countries engaged in disinformation increased from 48 to 70 or 150% from 2018 to 2019 (Samantha Bradshaw and Philip N. Howard, Oxford Internet Institute, 09/04/19). This is not about politics, this is about truth, appropriate technology, security improvements, and better public-private partnerships.
Fig. 3. Purported Russian Disinformation Flow (Samuel Morales, 11/08/19).
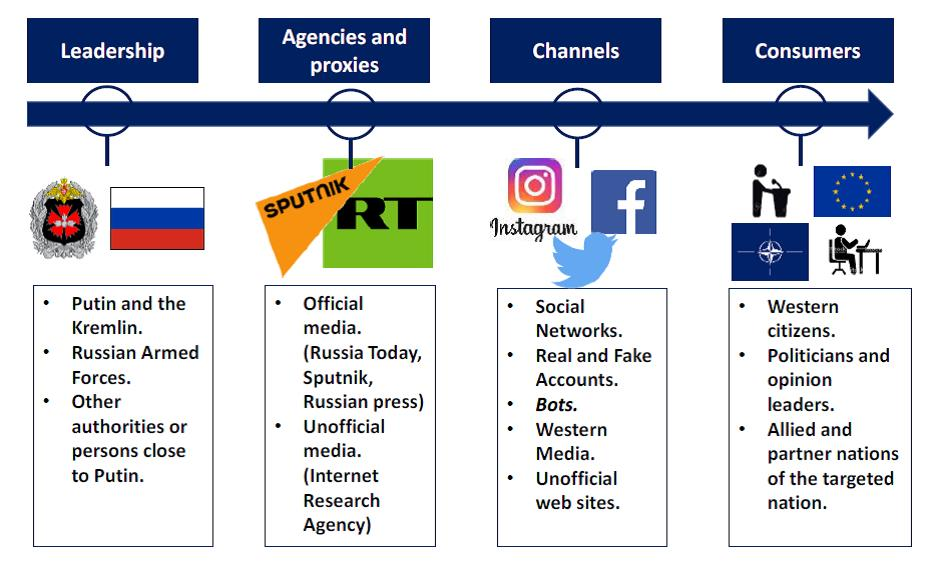
Moving on, large technology companies are increasingly under scrutiny to secure their platforms from disinformation campaigns. One recent example is as follows, “Twitter announced that it had removed more than 88,000 accounts that it said were engaged in “platform manipulation” originating in Saudi Arabia” (Aaron Holmes, Business Insider, 12/20/19). Since platforms like this have so much activity to monitor, many campaigns like this go on unaltered. Yet, let us not forget about the free speech rights of users and the many claims that certain tech companies are overreaching in their screening content to the level of undue bias. Resolving these two extremes is indeed a work in progress.
Another example which used AI (Artificial Intelligence) enabled disinformation is as follows: ‘“On December 20, 2019, Facebook took action against a network of over 900 pages, groups, and accounts on its own platform and on Instagram that were associated with “The Beauty of Life” (TheBL), reportedly an offshoot of the Epoch Media Group (EMG). These assets were removed for engaging in large-scale coordinated inauthentic behavior (CIB)”’ (Ben Nimmo, C. Shawn Eib, L. Tamora, et al; Graphika & the Atlantic Council’s Digital Forensics Research Lab, 12/2019). Many of these profiles were created with AI generated fake profile photos. The group amassed about 55 million followers, so their disinformation efforts largely worked.
Considering these disinformation events this past year, we think small and mid-size companies are likely the next target of disinformation campaigns. Such campaigns may aim to steal their customers, tarnish their reputation, or otherwise combine disinformation with advanced malware or other cyber fraud. They may be a direct target or a pass through medium. Small businesses are not immune from these risks even if never targeted before. While a large company could sustain several disinformation attacks, a small company could be easily run out of business by just one.
Imagine fraudulent Yelp reviews from a dental competitor who hires a non-U.S. based hacking group to have a bot army create 1,000 negative dental reviews on Yelp. Now the victim of this attack has a mess to clean up. Being a dental office, they are not tech experts, so they have to hire a tech consultancy. Yet even when hired, the full damage can never be undone. The stress and cost could drive them to shut down. Then there is the question of who pays for it? This begs the question of cyber insurance, do you have the correct coverage, is there any way your claims can be denied?
Overall, disinformation is a double-edged sword because if one country is using disinformation against another country, then that country is very tempted to use disinformation against them in response. Then when the public sees this state originated disinformation, they and their NGO (non-governmental organization) groups respond whether they believe the disinformation or not —of course with different responses. The same scenario could apply in a company to company context.
Disinformation is indeed a vicious cycle that encourages lies, ignorance, all the while damaging the value of what journalism means. In 2020 we as journalists, thought leaders, consultants and citizens must not be afraid to confront these fallacies and hidden distortions for future generations — a quality based truthful pen is a powerful sword!
2) Ransomware Doubles Attacking More Government Entities:
Ransomware heavily hit hospitals, businesses, and universities in 2019, but local governments were the top target. It attacked at least 103 local U.S. government agencies, mostly at the city and county levels (Emsisoft Malware Lab, 12/12/19). Further validating this conclusion is Barracuda Networks who found more broadly that two-thirds of all known 2019 ransomware attacks in the U.S. targeted U.S.governments (Alfred Ng, C-NET, 12/05/19). Specifically, these ransomware attacks originate mostly from phishing emails. Then the attackers implant malicious code in the targeted entities’ network, after which they encrypt their files making them inaccessible. These are for the most part not federal offices like the FBI, NSA, DOD, or the FAA — these offices have bigger budgets and better defenses.
In August 2019 twenty-three Texas cities were struck by a large coordinated ransomware attack. This overwhelmed them SO they were forced to seek advanced state assistance (Kate Fazzini, CNBC, 08/20/19). Also in 2019, seven Florida cities were struck in a similar attack: River City, Riviera Beach, Lake City, Key Biscayne, Stuart, Naples, and recently Pensacola (Rachael L Thomas, Naples Daily News, 08/20/19 & CISOMAG, 12/27/19). Moreover, the city of Baltimore, Maryland sustained two ransomware attacks in 14 months (Kate Fazzini, CNBC, 08/20/19). Fig. 4. shows the defaced City of New Orleans website which left citizens out of some services and information.
Fig. 4. City of New Orleans Website Down (NOLA.gov, City of New Orleans, 12/23/19).

Foolish as it may sound local governments are more frequently opting to pay the ransomware rather than rebuild their systems. After seeing Atlanta spend $2.6 million in 2018 to restore its systems rather than pay the $52,000 ransom (Lily Hay Newman, Wired, 04/23/18) — many officials have decided that it’s cheaper to pay the hackers. One researcher confirmed this as follows; ‘“These government organizations are not always well-equipped on cybersecurity concerns, which makes them easy targets,” said Kevin Latimore, enterprise malware removal specialist for security software provider Malwarebytes. “Not only do they have the potential to pay, but they are a soft target”’ (Alfred Ng, C-NET, 12/05/19). More examples of this include Lake City, Florida who paid $426,000 to hackers via Bitcoin, and Riviera Beach Florida who paid hackers $600,000 via Bitcoin in 2019. Much of this will be covered by their cyber insurance but it complicates future payouts making denials and premium increases more likely (Scottie Andrew and Saeed Ahmed, CNN, 06/27/19).
For the coming year, this means that local governments need to harden their networks, better train their staff and hire private-sector talent. If they have paid ransom ware once they should expect and prepare for another attack soon, yet this does not rush onboarding of new vendor tools as vendors need to be risk assessed. Moreover, they outsource key IT tasks when they cannot meet the required service or security. Lastly, paying ransomware is not a long-term solution and it increases the likelihood of another attack, plus there is no guarantee they have not copied your data.
3) Insurance Companies Paying Ransoms Are Likely Encouraging More Attacks for Profits:
When organizations have cyber insurance, they are more likely to pay ransom demands. This results in ransomware being more profitable than it would otherwise be and thus incentivizes more well-funded attacks (Emsisoft Malware Lab, 12/12/19). Yet if insurance companies did better due diligence reviewing prospect customer cyber risk processes, tools, SOC reports and the like — there would likely be less grounds for claims denials and fewer simple claims like ransomware, etc. In some cases, the customer is incented to prove their cyber due diligence to justify a favorable risk rating and lower insurance premiums. However, the rigor of this due diligence is inconsistently applied in favor of sizeable companies where more dollars and complex risk exists. Yet can you imagine being a large insurance company asking a government entity for any documentation like this… it might be difficult. Even small county governments often have many unhelpful bureaucrats who are overconfident thus choking the needed risk management process. Private companies have the same issue, but they have less bureaucratic insulation. Overall, better public-private partnerships are needed.
This year we confirmed that cyber liability insurance risk assessment is still a contradictory mess. The carriers are profit-driven while they often confuse customers on what a policy means, especially small and medium-sized businesses that are not tech-focused. The risk assessment standards are immature, not organization specific, and they are outdated with current technology. If ransomware incentivizes cyber insurance, then what about the likely situation where an organization gets hit with ransomware, then the carrier pays it less the deductible, but then the ransomware demands a second payment. Carriers, adjusters, risk assessors, and even companies have not thought this through well enough. Most likely the carrier will deny the second payment demand and often in tandem with costly litigation.
Whatever the size or your organization, you should undergo strict security reviews in the insurance underwriting process. If the carrier does not ask anything or much about your technology or security, you might as well not pay for the coverage because it’s weak at best. Whatever risk diligence completed in underwriting the coverage, you should not publicly disclose that you have such coverage because cyber extortionists could then view you as a target. Cyber insurance should not be considered as an alternative to adequately funded and resourced security programs, rather it’s a failsafe. Our related article from this summer clarifies some of these complexities 10 Things IT Executives Must Know About Cyber Insurance!
Fig. 5. Cyber Security Spending Greatly Outpaces Cyber Insurance Spending, (Gartner, Munich Re, Microsoft, Marsh, 2019)
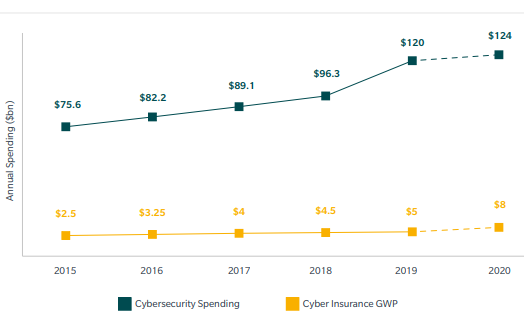
Lastly, we observed that cyber insurance spending is not growing as fast as cybersecurity spending from 2018 to 2019 (Fig 5). While for 2019 to 2020 there is a $116 billion dollar estimated difference (Fig 5.). This trend is generally good because you cannot insure away what you have not built securely in the first place. In physical security terms, that would be like a bank having wide open doors and windows often yet wanting to get robbery insurance when they are incenting robbery. Of course, this is far more complicated in cyberspace and insurance companies and risk assessors are moderately speculative at best. We anticipate more partnerships with tech-savvy insurance brokers in 2020, more cyber insurance training, and perhaps new FinTech insurance startups can reduce risk and drive efficiencies while the legislators and large companies catch up.
4) Mobile Ecosystem Security Considerations Multiply:
Since the release of the first iPhone in 2007, the appification of everything is the new norm. Since computing power and memory on smartphones nearly doubles about every two years (Gordon Moore’s Law, 1958); the information security risk on these devices gets more complicated and multiplies with each new app installed.
Here are some recent top metrics from one independent blog study (Ian Blair, BuildFire, 2019):
- There are 2.8 million apps available for download on the Google Play Store — More apps equals more risk exposure.
- The Apple App Store has 2.2 million apps available for download.
- Mobile apps are expected to generate $189 billion in revenue by 2020.
- 49% of people open an app 11+ times each day.
- 21% of Millennials open an app 50+ times per day.
- 57% of all digital media usage comes from mobile apps.
- The average smartphone owner uses 30 apps each month — Touching many or all of the mobile ecosystem components in Fig. 6. — Thereby increasing complexity.
Fig 6. Mobile Ecosystem Components (Rohit Kumar, 2019).
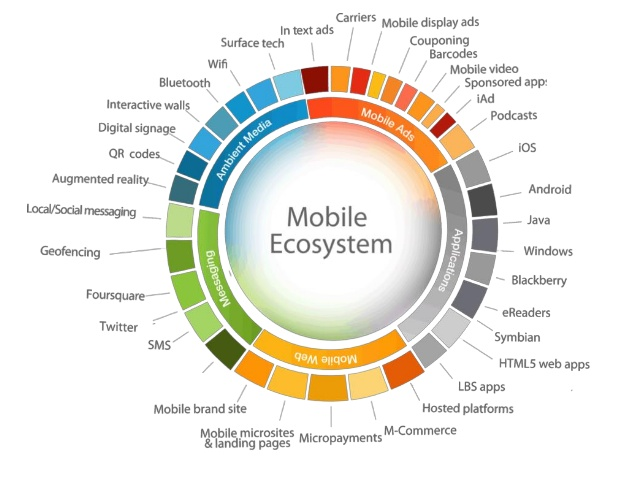
The Apple App Store has a closed API (application programming interface) and thus less apps, unlike the Google Play App Store which has an open API and more apps. Thus, in prior years Apple’s App Store was regularly perceived as more secure than Google’s Play Store. However, in the fall of 2019, a reported 18 malicious apps were able to bypass Apple’s vetting system. Wired described it as follows, “it started small. Wandera’s security software flagged some unusual activity on a client’s iPhone. A lone speedometer app had made unexpected contact with a so-called command and control server, which had previously been identified as issuing orders to ad fraud malware in a separate Android campaign. In other words, the app had gone rogue” (Brian Barrett, Wired, 10/25/19).
Although the new iPhone 11 has no CPU power increase from the prior version, the new Samsung Galaxy S 11 includes a CPU that raises the bar in some ways for both phones. The new CPU is the Qualcomm Snapdragon 865 and will come with the new Galaxy S 11 in 2020. This CPU is 5G enabled while older chips are not. It also supports up to 8K HD video which has an ultra-high resolution that translates into very large files (Jessica Dolcourt, C-Net, 12/19/19). This enables better video chat, HD gaming, and professional level photo capabilities.
Additionally, the Snapdragon 865’s two-finger biometric unlocking feature has been improved for the Galaxy S 11 thereby challenging the new iPhone 11. The CPU’s 3D Sonic Max fingerprint reader is large enough to register two fingers as one commentator detailed: “This means it’s faster to unlock, and more secure when matching up more unique data points in the form of the ridges, valleys, and pores unique to your fingers. On phones, you might get the option to set up one or two-finger unlocking, or perhaps choose to use dual-finger authentication for mobile payments only, or select apps like your banking app” (Jessica Dolcourt, C-Net, 12/19/19).
Faster CPUs in the mobile ecosystem means that there is more room for malvertising, rootkits, viruses and other exploits to hide. Combine that with the increasing number of apps users download, the permissions they give them, etc. The complexity of this increases privacy and security risk. There is a very fine line between a hacked system and consented to app permissions, yet most users have few details on what this means or how many apps they have on their mobile devices.
For 2020, we see education and awareness around the review and removal of non-essential mobile apps as a top priority. Especially for mobile devices used separately or jointly for work purposes. This begs the questions: 1) what is the best BYOD (bring your own device) policy 2) and good containerization to separate company vs. personal use apps? This requires better understanding around geolocation, QR code scanning, in text ads, micropayments, Bluetooth, geofencing, readers, and HTML5. It thus goes without saying that we feel more holes will be exposed with BYOD tools and policy as they gain more adoption 2020.
5) Cloud Adoption Raises Privacy and Compliance Concerns:
Cloud computing grew in 2019 and is expected to grow in the coming years. Many industries are opting for cloud computing because it is less costly than on-premises and the service quality is generally better. This especially applies to small and medium businesses that often don’t have the technology resources to build their own infrastructures. According to one study, “83% of enterprise workloads will be in the cloud by 2020” (LogicMonitor, 2019). As a result, many industries are increasing their investment in cloud computing and the costs are likely to go down as cloud providers improve — the services are being democratized via niche cloud service tool startups. At present, “50% of enterprises spend on average of $1.2 million dollars on cloud services annually” (LogicMonitor, 2019).
Although cloud computing might seem cheaper than on-premises solutions, it has its downsides when it comes to security and privacy. Moving to the cloud is accepting the risk of having your data in someone else’s warehouse. Of course, the service level agreement and vendor risk assessment compliance documents will address most of this, but it’s not comprehensive. This is because cloud vendors are selective about what they disclose to customers in their annual or quarterly vendor risk review. This is because they are protecting their own privacy and the privacy of their many other clients where shared infrastructure is relevant. If you want complete privacy and control, build your own cloud but accept the higher cost.
Fig. 7. Public Cloud Challenges Influencers Survey (LogicMonitor, 2019).
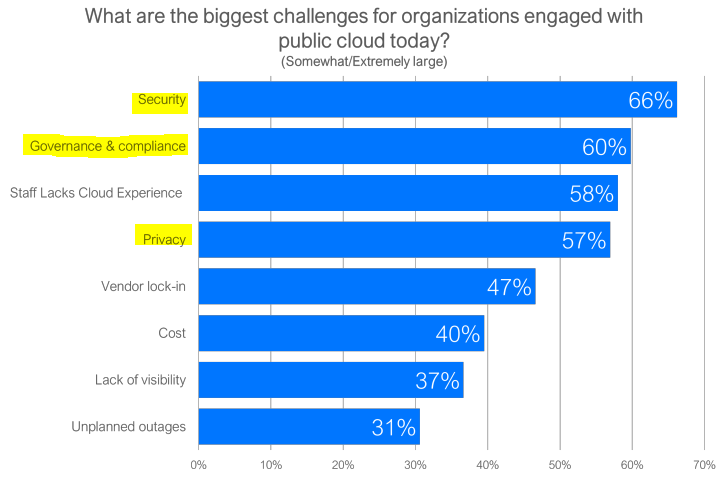
The above survey by a vendor Logic Monitor confirmed that security, governance and compliance, and privacy were top challenges in 2019. We think these challenges will hold steady in 2020, while costs will likely decrease for basic use cases. If organizations continue to struggle with cloud trained employees, it will negatively impact vendor lock-in. This can be bad from a failover perspective. We think organizations should spend more on cloud trained staff. They should also make sure that they are selecting more than two or three cloud providers, all separate from one another. This helps staff get cross-trained on different cloud platforms and add ons, but it also mitigates risk and makes vendors bid more competitively.
6) Supply Chain Cyber Security Threats Increase:
All organizations depend on other entities for goods and services. Everything from manufacturers, distributors, marketers, attorneys, drivers, resellers, software providers, accountants, and more. The flow of this from start to finish is called the supply chain, and vendor management is the biggest part of it. As a result, it becomes challenging for organizations to identify and assess the security of every vendor they do business with. In fact “at least 59% of organizations have suffered from cyberattacks through third-party companies” (Olivia Scott, Supply Chain Brain, 10/09/19). Depending on the vendor and the connection point there may be more or less steps. More steps increases complexity and often decreases transparency, which in turn often increases risk.
Every aspect of supply chain has an internet-connected component from UPS Package scanners, to invoice creation, inventory management, quality control, and more. Vendors who say or suggest they are not internet-connected are usually wrong because they forgot one thing like utility applications, HVAC applications, coffee machine apps, navigation apps, payment processing apps, and their own 3rd parties that have access to customer data via the vendor, etc.
People often need clarification on what is a 4th party vendor. They are the vendors that your 3rd party vendor contracts with to meet your needs. With a 4th party vendor, you will have less insight into their infrastructure and process, if at all. Most likely any risk documentation you get from them with come via your 3rd party vendor. A lot of misinformation and hidden risk is here. Vendors managers need good communication skills and business tact to deal with this.
In the context of cybersecurity, supply chain is posing a growing threat because most of the parts of our computers and smartphones are made in other parts of the world, including the software used to run these machines. For example, iPhone chips are made by Taiwan Semiconductor Manufacturing Company (TSMC) who works with other vendors for even the smallest of components in a highly complex supply chain, acting as a manufacturer and assembler. If there is a security hole in one of the iPhone components, the customer Apple may not be the first to know because TSMC or their 3rd and 4th party vendors may not know about it or may not disclose it. This negatively impacts Apple and iPhone users.
Observing this paradox, security pioneer Bruce Schneier stated, “the computers and smartphones you use are not built in the United States. Their chips aren’t made in the United States. The engineers who design and program them come from over a hundred countries. Thousands of people have the opportunity, acting alone, to slip a backdoor into the final product” (Bruce Schneier, New York Times, 09/25/19). Thus the supply chain path needs to be scrutinized for security compliance regularly, especially in the context of large-scale hardware manufacturing for data-centric products like smartphones, cars, computers, and medical devices — few devices are not data-centric these days.
In sum, supply chain is here to stay because organizations will need to collaborate with one another in order to conduct their business efficiently. According to the Ponemon Institute, 3rd party misuse was the second-biggest security threat in 2019 (Olivia Scott, Supply Chain Brian, 10/09/19). Yet we need a reminder that supply chain is no longer merely transportation and inventory management, even if we are a goods and services company like a small construction company with no website. We need to rethink of supply chain as more digital and more data-centric than we did in prior years. It is a part of core business operations.
Thus, supply chain security should be a top priority for organizations in 2020 with a focus on 3rd party risk ranking and 4th party identification. Lastly, for big entities like government and corporate conglomerates who have many different internal organizations they interact with. They would be well advised to think of their own internal procurement process as “external supply chain” in an effort to better training and internal defenses — they are often their own worst enemy.
About the Authors:

Mamady Konneh (left) is a senior information security professional, speaker and mentor with 10+ years of relevant experience in security, risk management, and project management in the healthcare, finance, and retail industries. He is a dynamic team player who leads by taking initiatives in developing efficient risk mitigation and situational awareness tactics. He is proficient at assessing the needs of the business and providing the tools to resolve challenges by enhancing the business process. He holds an MSST (Master of Science in Security Technologies) degree from the U of MN where he researched global I.D. card best practices for the country of Guinea.
Jeremy Swenson (right) is a senior IT consultant, writer, and speaker in business analysis, project management, cyber-security, process improvement, leadership, music, and abstract thinking. He has been employed by or consulted at many banks, insurance companies, retailers, healthcare orgs, governments, and so on over 14 years. He has an MBA from St Mary’s Univesity of MN and MSST (Master of Science in Security Technologies) degree from the U of MN.
