 This article reviews the 2014 Sony hack from a strengths and weaknesses standpoint based on select parts of the SysAdmin, Audit, Network and Security (SANS) and National Institute of Standards in Technology (NIST) frameworks. Although an older hack, the lessons learned here are still relevant today.
This article reviews the 2014 Sony hack from a strengths and weaknesses standpoint based on select parts of the SysAdmin, Audit, Network and Security (SANS) and National Institute of Standards in Technology (NIST) frameworks. Although an older hack, the lessons learned here are still relevant today.
Strengths – A Track Record of Innovation and Multilayered Information Security:
From early boom-boxes in the 1980s to the first portable disc player in the early 1990s. To high-quality headphones, the first HD TVs, to high-quality speakers, a gaming system revolution called the PlayStation, and now a massive on-line gaming network, Sony has been creative and innovative. This has made them one of the most respected and profitable Japanese companies to date. Yet this success derived overconfidence in other areas including information security but they still have the potential and the money to be a security leader. The managerial layering of Sony’s information security team was a good start even if their head count was too low. One source stated, “Three information security analysts are overseen by three managers, three directors, one executive director and one senior vice president” (Hill, 2014). Although contradictory, at least there was some oversight.
Failure 1 – Poor Culture and Lack of Leadership Support:
Sony’s leadership is on the record as not respecting the recommendations of either internal or external auditors. A quote from an I.T. risk consultancy summarized it this way, “The Executive Director of Information Security talked auditors out of reporting failures related to Access Controls which would have resulted in Sony being SOX (Sarbanes-Oxley) non-compliant in 2005” (Risk3sixty LLC, 2014). Things like this trickle down the layers of management and become a part of the company culture. Specifically, low level whistle blowers were silenced even though their I.T. risk arguments were solid. “Sony’s own employees complained that the network security was a joke. (Risk3sixty LLC, 2014)”. When this happened Sony’s leaders failed to execute their fiduciary duty to the board, shareholders, and customers. They did this so they did not look bad in the short term yet it cost the company more in the long term.
Failure 2 – Not Understanding Their Baseline:
The baseline is a measure that determines when you have the right amount of security and security process in relationship to your required business objectives and risk tolerance. Being below the baseline means risk is too high and an attack or breach is likely. This is why the baseline changes often and needs to be closely monitored. For example, when you are producing a very politically controversial movie about an unruly world leader who has a history of making war threats against his political opponents, you should have a higher baseline to be on guard from hacktivists. Sony overly focused on their cash generating core competencies and security was at most an afterthought. According to one source, Sony Pictures had just 11 people assigned to a top-heavy information security team out of 7,000 total employees (Hill, 2014). For a technology company that is way too few people working in security. It’s not enough people to collect and intelligently review logs, patch software, pen test, red team, and be available for one or more war room type projects which are bound to come up – all things prudent security would require.
Understanding your I.T. risk baseline requires testing and measurement and this has to be based on some framework, SANS, NIST, or some of the others. One former employee described Sony’s failure to comply with any framework as follows, “The real problem lies in the fact that there was no real investment in or real understanding of what information security is. One issue made evident by the leak is that sensitive files on the Sony Pictures network were not encrypted internally or password-protected” (Hill, 2014). Had they conformed to the SANS or NIST framework they would have been required to encrypt the data – see conclusion.
Failure 3 – Weak Password Policies:
Sony’s password policy was embarrassingly weak. In fact, so weak you might think they were deliberately trying to help hackers. “Employees kept plaintext passwords in Microsoft Word documents” (Franceschi-Bicchierai, 2014). Even very small companies from the 1990s would have policies against that. Moreover, one source confirmed that the word files were named with password in the file name (Risk3sixty LLC, 2014). Once in the network, all a hacker has to do is search for a file with password in the name and they have it.
Failure 4 – Late Detecting the Hack and Data Exfiltration:
Right away the intruders easily walked into Sony’s internal network and began stealing unencrypted sensitive data with apparently no log alarms going off. Sony had not followed data classification, retention, or governance plans – not even checkbox compliance. If they did they would not have had all types of data mixed together. One reporter described it this way, “Intruders got access to movie budgets, salary information, Social Security numbers, health care files, unreleased films, and more” (Hill, 2014). Thus, their network segmentation here must have been weak or non-existent. Health care data should not be near unreleased film files as they are totally different. There is no business justification for this. Segmenting and encrypting the data would have greatly reduced and delayed any data theft.
Conclusion:
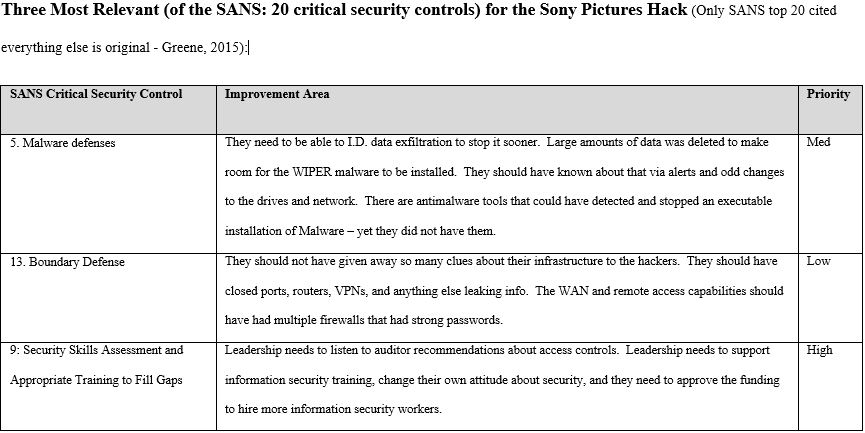
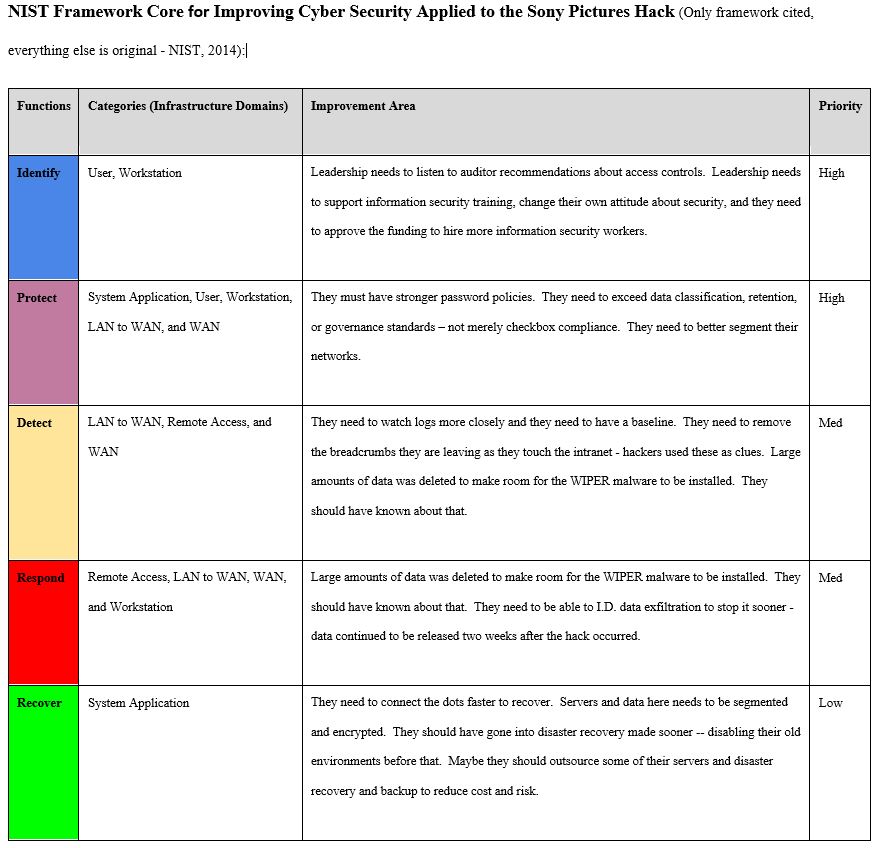
References:
Baker, L., & Finkle, J. “Sony PlayStation suffers massive data breach”. Reuters. Published 04/26/11. Viewed 10/26/16. http://www.reuters.com/article/2011/04/26/us-sonystoldendata-idUSTRE73P6WB20110426
Franceschi-Bicchierai, Lorenzo. “Don’t believe the hype: Sony hack not ‘unprecedented,’ experts say.” Mashable. Published 12/08/14. Viewed 10/20/16. http://mashable.com/2014/12/08/sony-hack-unprecedented-undetectable/#359BD06aEkq6
Greene, Tim. “SANS: 20 critical security controls you need to add.” Networked world. Published 10/13/15. Viewed 10/23/16. http://www.networkworld.com/article/2992503/security/sans-20-critical-security-controls-you-need-to-add.html
Hill, Kashmir. “Sony Pictures hack was a long time coming, say former employees”. Published 12/04/14. Viewed 10/20/16. http://fusion.net/story/31469/sony-pictures-hack-was-a-long-time-coming-say-former-employees/
NIST. “Framework for Improving Critical Infrastructure Cyber Security”. Published 01/01/2016. Viewed 10/23/16. https://www.nist.gov/sites/default/files/documents/cyberframework/Cybersecurity-Framework-for-FCSM-Jan-2016.pdf Risk3sixty LLC.
Risk3sixty. “The Sony Hack – Security Failures and Solutions.” Published 12/19/14. Viewed 10/20/16. http://www.risk3sixty.com/2014/12/19/the-sony-hack-security-failures-and-solutions/
Sanchez, Gabriel. “Case Study: Critical Controls that Sony Should Have Implemented”. SANS Institute Information security Reading Room. Published 06/01/2015. Viewed 10/20/16. https://www.sans.org/reading-room/whitepapers/casestudies/case-study-critical-controls-sony-implemented-36022
