By Jeremy Swenson, MBA, MSST & Angish Mebratu, MBA.
Every year we like to review and commentate on the most impactful technology and business concepts from the prior year. Those that are likely to significantly impact the coming year. Although incomplete, these are five areas worth addressing.
5. 5G Expansion Will Spur Business Innovation
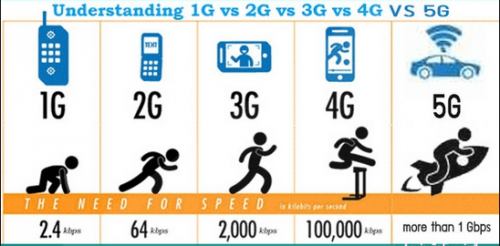
2018 was the year 5G moved from hype to reality, and it will become more widespread as the communications supply chain adopts it in 2019. 5G is the next iteration of mobile connectivity and it aims to be much faster and more reliable than 4G, 3G, etc. Impressively, data speeds with 5G are 10 to 100 times faster than 4G. The benefits of this includes enabling: smart IoT connected cities, seamless 8K video streaming, improved virtual reality styled gaming, self-driving cars that communicate with each other without disruption thereby enhancing safety and reliability, and improved virtual reality glasses (HoloLens, Google Glass, etc.) providing a new way of looking at the world around us.
As emerging technologies such as artificial intelligence (AI), blockchain, the Internet of Things (IoT), and edge computing — the practice of processing data near the edge of the network where the data is being generated, not a centralized data-processing repository — take hold everywhere, 5G can offer the advancements necessary to truly take advantage of them. These technologies require 5Gs bolstered data transfer speeds, interoperability, and its improved reliability. Homes will get smarter, hospitals will be able to provide more intelligent care, the Internet of Things will go into hyperdrive — the implications of 5G are massive. Yet most importantly, 5G has much less latency, thereby enabling futuristic real-time application experimentation.
“There’s no doubt that much of the recent 5G activity has been focused on investments from service providers and equipment manufacturers,” Nick Lippis, co-founder and co-chairman of the Open Networking User Group (Kym Gilhooly, BizTech, 11/08/18). “However, more IT leaders are starting to make plans for 5G, which includes determining its impact on their data center architecture, procurement strategies and the solutions they’ll roll out”(Kym Gilhooly, BizTech, 11/08/18).
AT&T is one of the leaders in 5G distribution and as of 12/27/18 they have service up and running in these 12 cities: Atlanta, Charlotte, Dallas, Houston, Indianapolis, Jacksonville, Louisville, Oklahoma City, New Orleans, Raleigh, San Antonio and Waco (CNN Wire, 12/27/18). Verizon has a similar initiative in an earlier phase in some cities. While Google has Google Fiber is some cities, but there is lots of debate about if its better or worse than 5G – time will tell. More data and faster speeds derive more connected devices which need security, data protection, and privacy — failure to protect it aggressively derives to much risk at high costs.
4. Browser/Device Fingerprinting Growth Will Spur Better PET (Privacy Enhancing Technologies)

Browser fingerprinting is a method in which websites gather bits of information about your visit including your time zone, set of installed fonts, language preferences, some plug-in information, etc (Bill Budington, Bennett Cyphers, Alan Toner, and Jeremy Gillula, Electronic Freedom Foundation, 12/22/18). These data elements are then combined to form a unique fingerprint that identifies your browser or more. The next step is to identify your specific device, and then you individually.
Device fingerprinting overcomes some of the inefficiencies of using other means of customer-tracking. Most notably, this includes cookies installed in web browsers, which businesses have long used monitor user behavior when we visit their websites (Bernard Marr, Forbes, 06/23/17). Employers do this at a much more invasive level, but the pay is the tradeoff. Yet when employees use their own mobile device for work-related things, protection of their personal data is best achieved via data containerization tools like AirWatch and Centrify. Even on these devices, the problem is that cookies can be deleted whenever we want. Its relatively easy for us to stop specific sites, services or companies from using them to track us — depending on how technical we are. Device fingerprinting doesn’t have this limitation as it doesn’t rely on storing data locally on our machines, instead, it simply monitors data transmitted and received as devices connect with each other” (Bernard Marr, Forbes, 06/23/17).
This type of data exploitation, even with the user’s consent, allows for more complexity and thus higher malware or SPAM/advertising risk. Antivirus makers are challenged to stay ahead of these exploits. The GDPR (General Data Protection Regulation) unequivocally states that this kind of personal data collection and user tracking is not permitted to override the “fundamental rights and freedoms of the data subject, including privacy” and is, we believe, not permitted by the new European regulation (Bill Budington, Bennett Cyphers, Alan Toner, and Jeremy Gillula, Electronic Freedom Foundation, 12/22/18). The high courts will validate this over time.
Further complicating the matter is the terms of service on data-centric technology platforms such as Facebook, Twitter, LinkedIn, WordPress, Instagram, Amazon, etc. Their business models require considerable data sharing with third and fourth-party business entities, who gather elements of specific user data and then combine them with other browser and device fingerprinting data elements, thus completing the dataset. All the while the data subject and interconnected entities are mostly clueless. This further complicates compliance, erodes privacy, but is great for marketers — many people appreciate that Amazon correctly suggests what they often desire. Yet that is not always a good thing because this starts to precondition a person or a culture to norms at the expense of originality. In the past we saw tobacco companies do this unethically targeting young people, and there are more examples — think for yourself.
This begs the question of who owns these datasets and at what point in their semblance, where are they stored, how are they protected, and to what extent can informed consumers opt out if practicable — observing there is be some incidental data collection that has business protection. This paradox spurs competition and the growth of privacy enhancing technologies (PETs). Existing PETs include communication anonymizers, shared bogus online accounts, obfuscation tools, two or three-factor authentication, VPNs (virtual private networks), I.P. address rotation, enhanced privacy ID (EPID), and digital signature algorithms (encryption) which support anonymity in that each user has unique public verification key and a unique private signature key. Often these PETs are more useful when used with a fake account or server (honeynet). This attempts to divert and frustrate a potential intruder but gives the defender valuable intelligence.
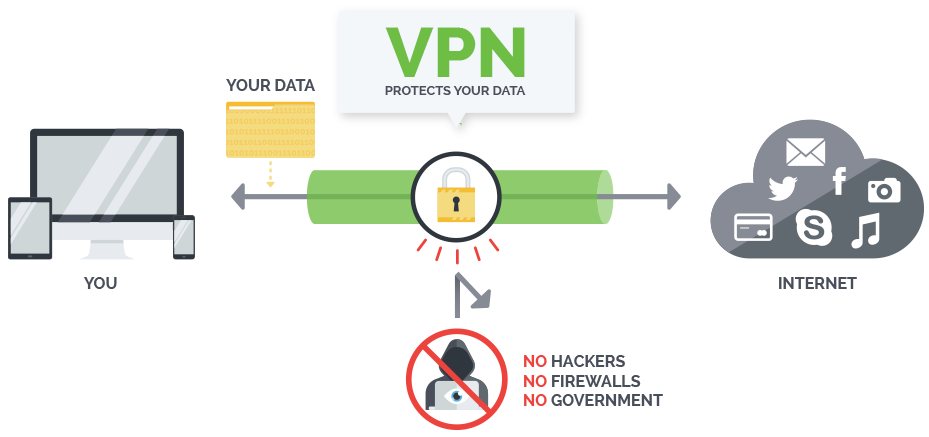
Opera, Tor and Firefox are leading secure browsers but there is an opportunity for better security and privacy plugins from the Chrome (Google) browser, while VPN (Virtual Private Network) technologies should be used at the same time for added privacy. These technologies are designed to limit tracking and correlation of users’ interactions with third-party entities. Limited-disclosure (LD) often uses cryptographic-techniques (CT) which allows users to retrieve only data that is vetted by providers, for which the transmitted data to the third party is trusted and verified.
3. Artificial Intelligence Will Grow on The SMB (Small and Medium Business) and Individual Market
In the past artificial intelligence (AI) has been primarily the plaything of big tech companies like Amazon, Baidu, Microsoft, Oracle, Google, and some well-funded cybersecurity startups like Cylance. Yet for many other companies and sects of the economy, these AI systems have been too expensive and too difficult to roll out effectively. Heck, even machine learning and big data analytics systems can be cost and time prohibitive for some sects of the economy, and for sure the individual market in prior years. However, we feel the democratizing of cloud-based AI and machine learning tools will make AI tools more accessible to the SMB and individual market.
At present, Amazon dominates cloud AI with its AWS (Amazon Web Services) subsidiary. Google is challenging that with TensorFlow, an open-source AI library that can be used to build other machine-learning software. TensorFlow was the Machine Learning behind suggested Gmail smart replies. Recently Google announced their Cloud AutoML, a suite of pre-trained systems that could make AI easier to use (Kyle Wiggers, Venture Beat, 07/28/18). Additionally, “Google announced Contact Center AI, a machine learning-powered customer representative built with Google’s Dialogflow package that interacts with callers over the phone. Contact Center AI, when deployed, fields incoming calls and uses sophisticated natural language processing to suggest solutions to common problems. If the virtual agent can’t solve the caller’s issue, it hands him or her off to a human agent — a feature Google labels “agent assist” — and presents the agent with information relevant to the call at hand” (Kyle Wiggers, Venture Beat, 07/28/18).
The above contact center AI and chatbots can both be applied successfully to personal use cases such as medical triaging, travel assistance, self-harm prevention, translation, training, and improved personal service. Cloud platforms and AI construction tools like the open source TensorFlow will enable SMBs to optimize insurance prices, model designs, diagnosis and treat eye conditions, and build intelligence contact center personas and chatbots, and much more as technology evolves in 2019.
2. Useful Big Data Will Make or Break Organizational Competitiveness
Developed economies increasingly use big data-intensive technologies for everything from healthcare decisioning to geolocation to power consumption, and soon the world will to. From traffic patterns, to music downloads to web service application histories and medical data. It is all stored and analyzed to enable technology and services. Big data use has increased the demand for information management companies such as, Oracle, Software AG, IBM, Microsoft, Salesforce, SAP, HP, and Dell-EMC — who themselves have spent billions on software tools and buying startups to fill their own considerable big data analytics gaps.
For an organization to be competitive and to ensure their future survival a “must have big data goal” should be established to handle the complexity of the ever-increasing massive volume of both, structured (rows and table) and unstructured (images and blobs) data. In most enterprise organizations, the volume of data is too big, or it moves too fast or it exceeds current processing capacity. Moreover, the explosive growth of the Internet of Things (IoT) devices provides new data, APIs, plugins/tools, and thus complexity and ambiguity.
We know there are open source tools that will likely improve reliability in big data, AI, service, and security contexts in 2019. For example, Apache Hadoop is well-known for its capabilities for huge-scale data processing. Its open source big data framework can run on-prem or in the cloud and has very low hardware requirements (Vladimir Fedak, Towards Data Science, 08/29/18). Apache Cassandra is another big data tool born out of Facebook around 2010. It can process structured data sets distributed across a huge number of nodes across the world. It works well under heavy workloads due to its architecture without single points of failure and boasts unique capabilities no other NoSQL or relational database has. Additionally it features, great liner scalability, simplicity of operations due to a simple query language used, constant replication across nodes, and more (Vladimir Fedak, Towards Data Science, 08/29/18).
For 2019 organizations should consider big data a mainstream quality business practice. They should utilize and research new tools and models to improve their big data use and applications — creating a center of excellence without being married to buzzwords or overly weak certifications that all too often squash disruptive solutioning. Lastly, these centers of excellence need to be dominated not by the traditional IT director overloads. Rather, the real people between the cracks who know more and have more creative ideas than these directors who often build yes clichés around themselves and who are often not the most qualified — great ideas and real leaders defy title.
1. Election Disinformation and Weak U.S. Polling Systems Harms Business and Must Be Fixed
The intersection of U.S. politics and media can be at times nasty, petty, selfish, or worse outright lies and dirty smear campaigns under shadow proxies who skirt campaign finance laws by being either a policy advocacy group – non-political, or worse yet, a foreign-sponsored clandestine intelligence agency of an enemy to the nation whose only rule is to disrupt U.S. elections. Perhaps Russian, North Korea, or even China affiliated groups.
Innovations in big data and social media, browser proxies and fiber optic cable, 5G, in conjunction with the antiquated and insecure U.S. polling system, makes election news and security complicated, fragile and highly important. At present, there are few people and technology companies that can help resolve this dilemma. For a state-sponsored hacker group altering a U.S. election is the ultimate power play.
Respect for all parties is a must and disinformation of any type should not be tolerated. Universities, think tanks, startups, government, and large companies need to put time and money into experimenting as to how we can reduce disinformation and better secure the polling systems. The first step is public awareness and education on checking purported news sources, especially those from digital media. The second step is more frequent enforcement of slander laws and policies. Lastly, we should hold technology companies to high media ethics standards and should write to their leaders when they violate them.
As for securing the polling systems, multi-factor authentication should be used, and voting should be done digitally via secure encrypted keys. If Amazon can securely track the world’s purchases of millions of products with way more data and complexity, and with service a moon shot better than your local state DMV (driver and motor vehicle) office, than the paper ballot and OCR (Optical Character Recognition) scanners need to go. There are many Android and iOS applications that are more secure, faster, and easier to use than the current U.S. polling system and they are doing more complex things and with more data that is changing at an exponentially faster rate. They were also made for less money. Shame on the U.S. OCR election system.
Business should not be afraid to talk about this, because, like a poisonous malware, it will spread and be used to easily run businesses out of business – often due to greed and/or petty personal differences. Examples of this include hundreds or thousands of fraudulent negative Yelp reviews, driving a competitor’s search rankings down or to a malicious site, redirecting their 1-800 number to a travel scam hotline, spreading false rumors, cyber-squatting, and more. Let 2019 be the year we stand to innovate via disruptive technologies for a more ethical economy.
About the Authors:

Mr. Swenson, MBA, MSST & Mr. Mebrahtu, MBA meet in graduate business school where they collaborated on global business projects concerning leadership, team dynamics, and strategic innovation. They also worked together at Optum / UHG. Mr. Swenson is a seasoned (14 years) IT consultant, writer, and speaker in business analysis, project management, cyber-security, process improvement, leadership, music, and abstract thinking. Over 15 years Mr. Mebrahtu has worked with various fortune 500 companies including Accenture and Thomson Reuters, and he is currently principal quality engineer/manager at UnitedHealthcare. He is also an expert in software quality assurance, cybersecurity technologies, and design and architecture of technology frames.
