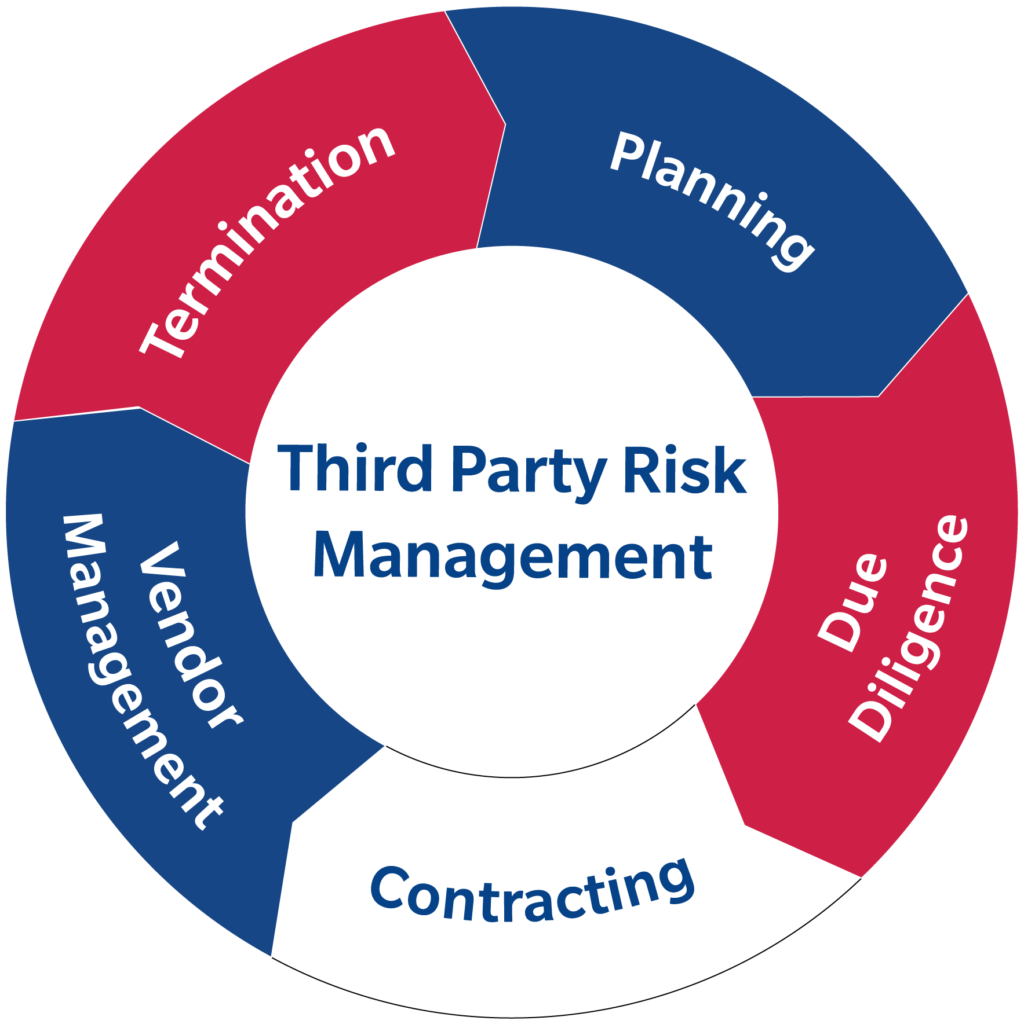
In this increasingly complex security landscape with threat actors and vendors changing their tools rapidly, managing third-party risk is very difficult, ambiguous, and it’s even more difficult to know how to prioritize mitigation spend. Thus, it’s not surprising that a 2017 Ponemon Institute vendor risk management survey across many industries concluded that 17% of the participants were not at all effectively managing these security risks (Maureen McKinney, 2018).
The key to any vendor risk management program or framework is measurement, repeatability, and learning or improving from what was repeated as the business and risks change. These are the nine best practices you can follow to help assess your vendors’ security processes and their willingness to understand your risks and collectively mitigate both of them.
1) Identify All Your Vendors / Business Associates:
Many companies miss this easy step. Use RBAC (role-based access controls) when applicable – windows groups or the like. Create a repeatable, written, compliance process for identifying them and make updates to the list as vendors move in and out of the company.
2) Ensure Your Vendors Perform Regular Security Assessments:
Risk assessments should be conducted on a weekly, monthly, or quarterly basis and reviewed and updated in response to changes in technology and the operating environment.
At a minimum, security risk assessments should include:
a) Evaluate the likelihood and potential impact of risks to in scope assets.
b) Institute measures to protect against those risks.
c) Documentation of the security measures taken.
Vendors must also regularly review the findings of risk assessments to determine the likelihood and impact of the risk that they identify, as well as remediate any deficiencies.
3) Make Sure Vendors Have Written Information Security Policies / Procedures:
a) Written security policies and procedures should clearly outline the steps and tasks needed to ensure compliance delivers the expected outcomes.
b) Without a reference point, policies and procedures can become open to individual interpretation, leading to misalignment and mistakes. Verify not only that companies have these written policies, but that they align with your organization’s standards. Ask other peers in your industry for a bench mark.
4) Verify That Vendors Encrypt Data in All Applicable Places – At Rest, In Transit, etc:
a) Encryption, a process that protects data by making it unreadable without the use of a key or password, is one of the easiest methods of protecting data against theft.
b) When a vendor tells you their data is encrypted, trust but verify. Delve deeper and ask for details about different in-transit scenarios, such as encryption of backup and what type of backup. Ask them about what type of encryption it is and get an infographic. Most people get lost when you ask this question.
c) It’s also imperative that the keys used to encrypt the data are very well-protected. Understanding how encryption keys are protected is as vital as encryption itself.
i) Are they stored on the same server?
ii) Is multi-factor authentication needed to get access to them?
iii) Is there a time limit on how long they can have access to the key?
5) Ensure Vendors Have A Disaster Recovery Program:
In order to be compliant with the HIPAA Security Rule and related rules, vendors must have a detailed disaster recovery program that includes analysis on how a natural disaster—fire, flood or even a rodent chewing through cables—could affect systems containing ePHI. The plan should also include policies and procedures for operating after a disaster, delineating employees’ roles and responsibilities. Finally, the plan should clearly outline the plan for restoring the data.
6) Prioritize Vendors Based on Risk – Use Evidence and Input from Others – NOT Speculation:
a) Critical Risk: Vendors who are critical to your operation, and whose failure or inability to deliver contracted services could result in your organization’s failure.
b) High Risk: Vendors (1) who have access to customer data and have a high risk of information loss; and / or (2) upon whom your organization is highly dependent operationally.
c) Medium Risk: Vendors (1) whose access to customer information is limited; and / or (2) whose loss of services would be disruptive to your organization.
d) Low Risk: Vendors who do not have access to customer data and whose loss of services would not be disruptive to your organization.
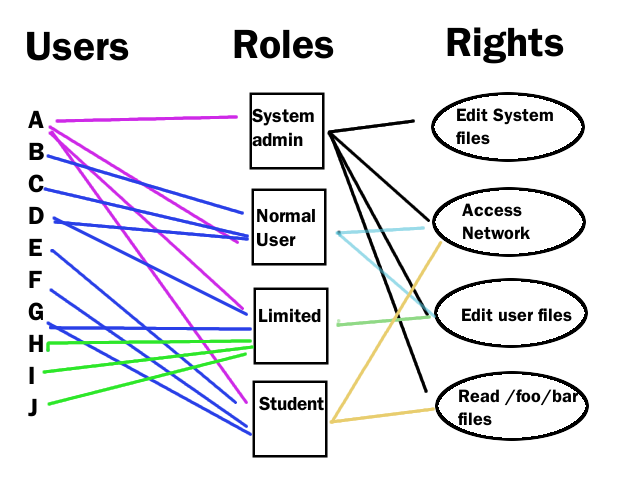
7) Ensure Access Is Based on Legitimate Business Needs:
It’s best to follow the principle of least privilege (POLP), which is the practice of limiting access rights for users to the bare minimum permissions they need to perform their work. Under
8) Vet All New Vendors with Due Diligence:
a) Getting references.
b) Using a standard checklist.
c) Performing a risk analysis and determining if the vendor will be ranked Critical, High, Medium or Low.
d) Document and report to senior management.
9) Ensure All Contracts Are Reviewed with Legal and Risk Counsel:
a) Requirements to keep system and data secure per best practices and industry standards.
b) Requirements to provide you access to audit documents.
c) Confidentiality and privacy requirements – GDPR, CA, and NY privacy rules.
d) Requirements to notify you of security breaches, incidents, and vulnerabilities. Quantify what these terms mean as there is lots of ambiguity dependent on the industry and use case. Identify who is the decider of if something is an event or incident.
e) Requirements to undergo independent penetration tests and vulnerability (scans) assessments.
Contact us here to learn more.
