Backing up data is one of the best things you can do to improve your response to ransomware, a data breach, an infrastructure failure, or other type of cyber-attack. Without a good comprehensive backup method that works and is tested, you likely will not be able to recover from where you left off thereby harming your business and customers.
The 3-2-1 backup method requires saving multiple copies of data on different device types and in different locations. More specifically, the 3-2-1 method follows these three requirements:
Fig. 1. 3-2-1 Backup Image, Stock, 2023.
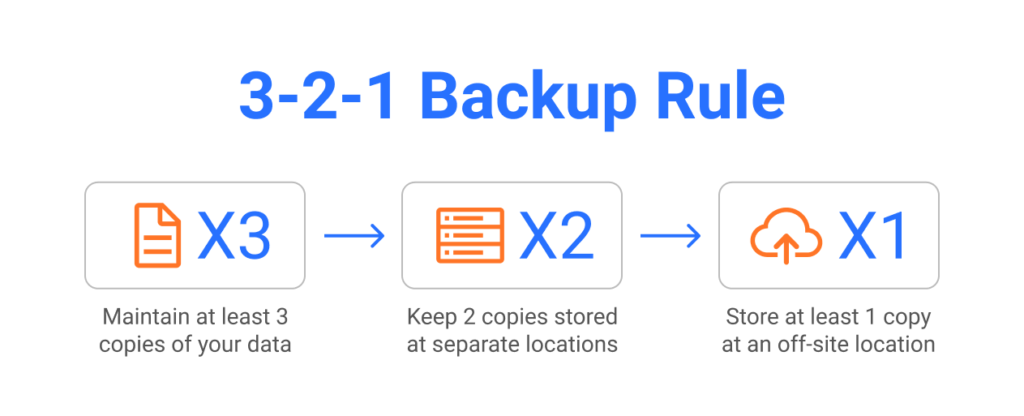
- 3 Copies of Data: Have three copies of data—the original, and at least two copies.
- 2 Different Media Types: Use two different media types for storage. This can help reduce any impact that may impact one specific storage media type more than the other.
- 1 Copy Offsite: Keep one copy offsite to prevent the possibility of data loss due to a site-specific failure.
Here are some pointers to make your backup more effective:
- Select the right data to back up: Critical data includes word processing documents, electronic spreadsheets, databases, financial files, human resources files, and accounts receivable/payable files. Not everything is worth backing up as it’s a waste of space. For example, data that is 8 years old with no business use is not worth backing up.
- Backup on a schedule: Backup data automatically on a repeatable schedule, if possible, bi-weekly, weekly, or even daily if needed. Pick a day or time range when the backup will run, say Thursdays at 10:00 p.m. CST (when most users are not working.
- Have backup test plans and follow them: Your backup plan must be written down in a clear and detailed way describing the backup process, roles, interconnections, and milestones which can gauge if it’s working, as well as the service time to recovery expected. Then of course test the backup at least every six months or after a key infrastructure change happens.
- Automate backups: Use software automation to execute the backups to save user time, and to reduce the risk of human error.
About the Author:
Jeremy Swenson is a disruptive-thinking security entrepreneur, futurist/researcher, and senior management tech risk consultant. Over 17 years he has held progressive roles at many banks, insurance companies, retailers, healthcare orgs, and even governments including being a member of the Federal Reserve Secure Payment Task Force. Organizations relish in his ability to bridge gaps and flesh out hidden risk management solutions while at the same time improving processes. He is a frequent speaker, published writer, podcaster, and even does some pro bono consulting in these areas. As a futurist, his writings on digital currency, the Target data breach, and Google combining Google + video chat with Google Hangouts video chat have been validated by many. He holds an MBA from St. Mary’s University of MN, an MSST (Master of Science in Security Technologies) degree from the University of Minnesota, and a BA in political science from the University of Wisconsin Eau Claire.
