As crypto-currency enters the mainstream cyber-criminals are using crypto-mining malware (Fig. 1) to infect websites and devices ranging from smartphones to servers. All of this is dependent on a strong understanding of bitcoin mining in the blockchain as described below.
Fig. 1. Bitcoin Crypto-Jacking Threat Actor.
Every ten to fifteen minutes mining computers collect hundreds of waiting bitcoin transactions (a block) and then convert them into mathematical puzzles. The first miner to find the puzzle solution shares it with others on the network. Then other miners check whether the sender of the funds has the right to spend the money and if the solution to the puzzle is correct. If enough of them grant their approval, the block is crypto-graphically added to the ledger and the miners move on to the next set of transactions (hence the term “blockchain”). The miner who found the solution gets 12.5 bitcoins as a reward (presently), but only after another 99 blocks have been added to the ledger. This is the incentive to participate in the system and validate these transactions (L.S., The Economist, 2015).
Clever as it may be, this system has weaknesses. One is rapid consolidation. Most mining power today is provided by pools—big groups of miners who combine their computing power to increase the chance of winning the coin reward. As mining pools have gotten bigger, it no longer seems inconceivable that one of them might amass enough capacity to mount a 51% attack—whereby an organization is somehow able to control most of the network mining power (hashrate). Bitcoin is secured by having all miners (computers processing the networks transactions). Indeed, in June 2014 one pool, GHash.IO, had the bitcoin community running scared by briefly touching that level before some users voluntarily switched to other pools.
As the bitcoin price continues to fall, consolidation could become more of a problem. Some miners are giving up because the rewards of mining no longer cover the costs. Some worry that mining will become concentrated in a few countries where electricity is cheap, like China, thus allowing a hostile government to seize control of bitcoin. Others predict that mining will end up as a monopoly—the exact opposite of the decentralized system that the elusive Bitcoin founder Mr. Nakamoto set out to create.
Fig. 2. General Crypto-Jacking Attack Flow. (Sugata Ghosh, ET Bureau, 05/11/2018).
 With a strong understanding of blockchain technology, crypto-mining malware attacks and infects websites and devices ranging from smartphones to servers in one of these three common but not exhaustive ways:
With a strong understanding of blockchain technology, crypto-mining malware attacks and infects websites and devices ranging from smartphones to servers in one of these three common but not exhaustive ways:
1) Sneaking dedicated crypto-mining software into your network via unpatched and out of date server vulnerabilities. Servers are especially at risk here: the crooks love them because they’re usually more powerful than desktops and laptops, and they’re usually running 24/7. Old mid-sized data centers are at high risk because they often have minimal defenses.
2) Sneaking JavaScript crypto-mining software into hacked web pages via cross side scripting (forms and comment fields) and WordPress plug-in vulnerabilities—hard to keep track of because there are so many. Then your browser mines for currency as you surf the web. The crooks get much less out of each victim – as soon as you leave the poisoned website, the mining stops – but a single hacked site could end up crypto-jacking millions of visitors each day, whatever operating system they’re using.
3) Mobile application exploits—twenty-four Android apps recently (Sept 2018) made it into the Google Play store with code that turns users’ phones into crypto-currency mining workers. Some of them targeted users in the US by using the guise of educational tools—they have been download around 120,000 times (Bleeping Computer, Ionut Ilascu, 09/28/18).
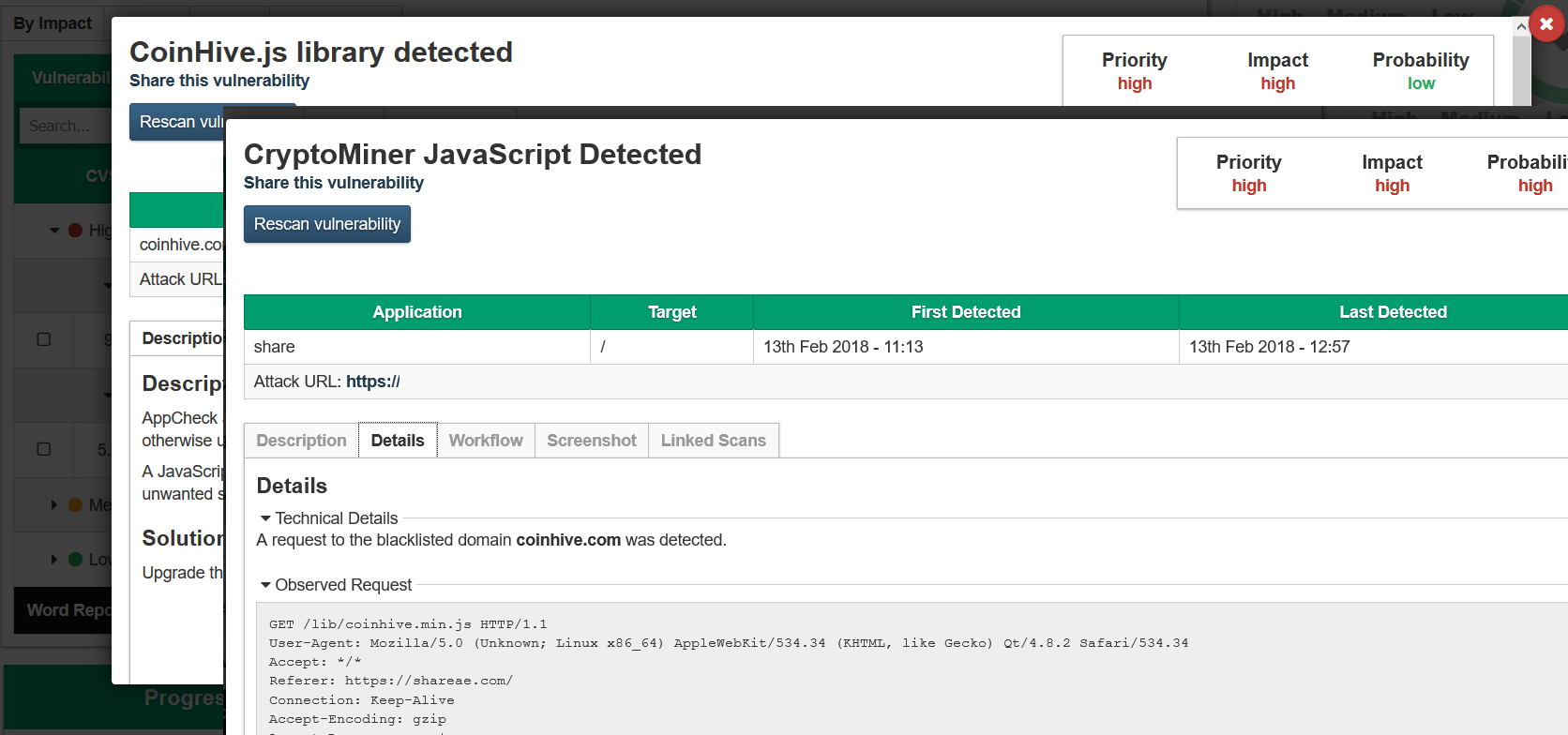
Crypto-jacking malware on enterprises running thousands of computers can disturb the daily operations of the business and even damage the hardware. In February 2018, Crypto-currency mining malware CoinHive was found on more than 5,000 government websites (Fig. 3) in the U.K., U.S., and Australia (Patrick Greenfield, The Guardian, 02/11/18). At present, CoinHive is easy to deploy and generated hundreds of thousands in its first month, so its arguably easy money for the attacker. In support of this conclusion RWTH Aachen University in Germany added: “embedded crypto-currency miner CoinHive is generating $250 thousand worth of Monero every month – most of it going to just 10 individuals. Moreover, they found that Monero accounts for 75 percent of all browser-based crypto-currency mining (David Canellis, TNW, 08/14/2018).
Once infected, the crypto-mining malware uses hosts CPU / GPU power to mine coins thus allowing cyber-criminals to grow their personal wallets. According to McAfee Labs crypto-mining malware attacks increased by 1,189% in Q1 2018. Attackers are getting smarter, instead of a one-time payment from ransomware, they prefer the long game and a steady revenue stream from infected devices (McAfee Labs Threats Report, June 2018). Crypto-mining is in its infancy and thus there’s a lot of room for growth and evolution over the next few years.
Fig. 3. CoinHive JavaScript Crypto-jacking Malware (GitHub).
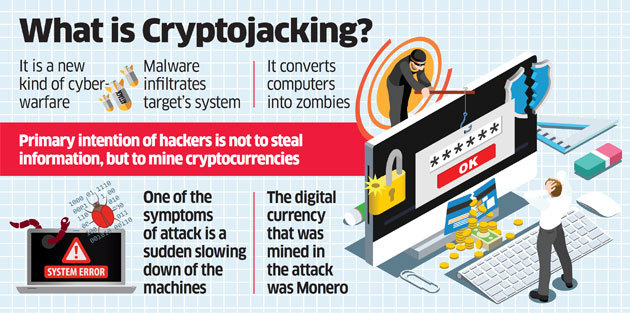
Oftentimes crypto-jacking goes undetected as attackers find new ways to infect the devices.
Yet here are the top three indicators that a machine is infected with crypto-malware:
1. Device is acting unusually slow.
2. Smartphone or personal computer constantly overheats.
3. Battery on laptop or phone dies unreasonably fast.
In today’s threat landscape here are the top five things you can do to prevent crypto-jacking:
1. Run most up-to-date anti-malware and antivirus programs. A strong one like Avast.
2. If your device significantly slows down when you’re on a certain site close it and
check it again. It may be an infected website especially if you get a bunch on pop-ups.
3. Install web browser anti-crypto-mining extensions.
4. Use AI driven network monitoring software (SecBl, Darktrace, etc). Mostly for servers not individual PCs.
5. Disable JavaScript to prevent in-browser crypto-jacking. On side effect is that you will not be able to view all sites in an optimal way.
By Jeremy Swenson & Andrew Erkomaishvili